Apple’s AirTags have caused a stir, but for all the wrong reasons. First, they turn all iPhones into Bluetooth LE beacon repeaters, without the owner’s permission. The phones listen for the AirTags, encrypt their location, and send the data on to the iCloud, where the tag’s owner can decrypt the location and track it down. Bad people have figured out that this lets them track their targets without their knowledge, turning all iPhone users into potential accomplices to stalkings, or worse.
Naturally, Apple has tried to respond by implementing some privacy-protecting features. But they’re imperfect to the point of being almost useless. For instance, AirTags now beep once they’ve been out of range of their owner’s phone for a while, which would surely alert the target that they’re being tracked, right? Well, unless the evil-doer took the speaker out, or bought one with the speaker already removed — and there’s a surprising market for these online.
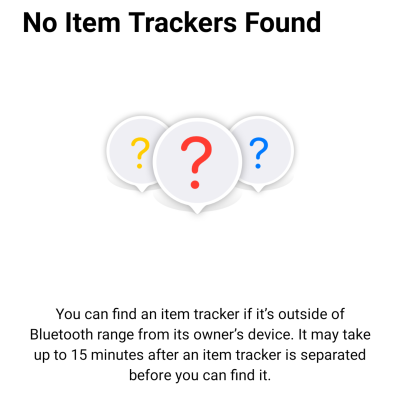 If you want to know that you’re being traced, Apple “innovated with the first-ever proactive system to alert you of unwanted tracking”, which almost helped patch up the problem they created, but it only runs on Apple phones. It’s not clear what they meant by “first-ever” because hackers and researchers from the SeeMoo group at the Technical University of Darmstadt beat them to it by at least four months with the open-source AirGuard project that runs on the other 75% of phones out there.
If you want to know that you’re being traced, Apple “innovated with the first-ever proactive system to alert you of unwanted tracking”, which almost helped patch up the problem they created, but it only runs on Apple phones. It’s not clear what they meant by “first-ever” because hackers and researchers from the SeeMoo group at the Technical University of Darmstadt beat them to it by at least four months with the open-source AirGuard project that runs on the other 75% of phones out there.
Along the way, the SeeMoo group also reverse engineered the AirTag system, allowing anything that can send BLE beacons to play along. This opened the door for [Fabian Bräunlein]’s ID-hopping “Find You” attack that breaks all of the tracker-detectors by using an ESP32 instead of an AirTag. His basic point is that most of the privacy guarantees that Apple is trying to make on the “Find My” system rely on criminals using unmodified AirTags, and that’s not very likely.
To be fair, Apple can’t win here. They want to build a tracking network where only the good people do the tracking. But the device can’t tell if you’re looking for your misplaced keys or stalking a swimsuit model. It can’t tell if you’re silencing it because you don’t want it beeping around your dog’s neck while you’re away at work, or because you’ve planted it on a luxury car that you’d like to lift when its owners are away. There’s no technological solution for that fundamental problem.
But hackers are patching up the holes they can, and making the other holes visible, so that we can at least have a reasonable discussion about the tech’s tradeoffs. Apple seems content to have naively opened up a Pandora’s box of privacy violation. Somehow it’s up to us to figure out a way to close it.