Many readers will be familiar with Microchip’s ATtiny85, which has been a popular choice for DIY projects in the past for its low price and (for the time) small size. But those looking for a more modern and capable 8-bit chip may find the ATtiny1616-MNR of interest. It offers expanded flash storage, more GPIO, and ditches SPI programming in favor of UPDI — a protocol that can be done using nothing more than an USB-UART converter and a resistor.

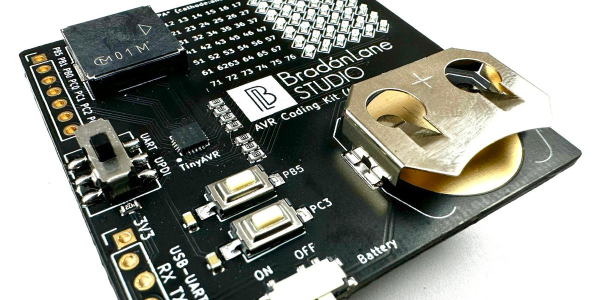
But here’s the catch: the new chip is only available in SMD and there are far fewer tutorials for it! That’s why [Bradán Lane] has created ACK1, a cute little AVR Coding Kit for those of us who want to play with the ATtiny1616 and a companion for his free and open-source course.
The board contains an array of 6 by 7 LEDs in a charlieplexed configuration, a large piezo buzzer, two push buttons, an on/off switch, and a CR2032 battery holder to keep it on without the need for a cable. The kit looks gorgeous in its white-on-black theme with gold plated contacts and can be had for $20 on Tindie at the time of writing.
The ATtiny1616 itself runs at up to 20 MHz and has 17 GPIO pins, 16 KiB of flash storage, 2 KiB of RAM, and 256 bytes of EEPROM for configuration — making it roughly on par with the original Arduino Uno.
The course that goes hand-in-hand with the ACK1 is all about the features of the ATtiny1616, from the basics of using the programmer to reading the buttons, using timers, driving the charlieplexed LEDs, storing data in the EEPROM and much more. Though it does not cover the basics of C, the course is free, and even licensed MIT, so that anyone can share it and improve upon it.
If you enjoy seeing beautiful microcontrollers, you’ll definitely want to see the stylish Uno Plus+.