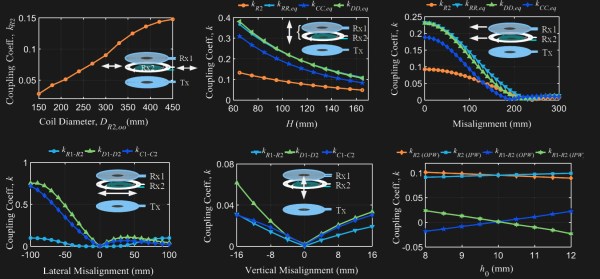
Join us on Wednesday, June 3 at noon Pacific for the Physical Security Hack Chat with Deviant Ollam!
You can throw as many resources as possible into securing your systems — patch every vulnerability religiously, train all your users, monitor their traffic, eliminate every conceivable side-channel attack, or even totally air-gap your system — but it all amounts to exactly zero if somebody leaves a door propped open. Or if you’ve put a $5 padlock on a critical gate. Or if your RFID access control system is easily hacked. Ignore details like that and you’re just inviting trouble in.
Once the black-hats are on the inside, their job becomes orders of magnitude easier. Nothing beats hands-on access to a system when it comes to compromising it, and even if the attacker isn’t directly interfacing with your system, having him or her on the inside makes social engineering attacks that much simpler. System security starts with physical security, and physical security starts with understanding how to keep the doors locked.
 To help us dig into that, Deviant Ollam will stop by the Hack Chat. Deviant works as a physical security consultant and he’s a fixture on the security con circuit and denizen of many lockpicking villages. He’s well-versed in what it takes to keep hardware safe from unauthorized visits or to keep it from disappearing entirely. From CCTV systems to elevator hacks to just about every possible way to defeat a locked door, Deviant has quite a bag of physical security tricks, and he’ll share his insights on keeping stuff safe in a dangerous world.
To help us dig into that, Deviant Ollam will stop by the Hack Chat. Deviant works as a physical security consultant and he’s a fixture on the security con circuit and denizen of many lockpicking villages. He’s well-versed in what it takes to keep hardware safe from unauthorized visits or to keep it from disappearing entirely. From CCTV systems to elevator hacks to just about every possible way to defeat a locked door, Deviant has quite a bag of physical security tricks, and he’ll share his insights on keeping stuff safe in a dangerous world.
Our Hack Chats are live community events in the Hackaday.io Hack Chat group messaging. This week we’ll be sitting down on Wednesday, June 3 at 12:00 PM Pacific time. If time zones have you down, we have a handy time zone converter.
Click that speech bubble to the right, and you’ll be taken directly to the Hack Chat group on Hackaday.io. You don’t have to wait until Wednesday; join whenever you want and you can see what the community is talking about.