If a couple of generations of spy movies have taught us anything, it’s that secret agents get the best toys. And although it may not be as cool as a radar-equipped Aston Martin or a wire-flying rig for impossible vault heists, this DIY TEMPEST system lets you snoop on computers using secondary RF emissions.
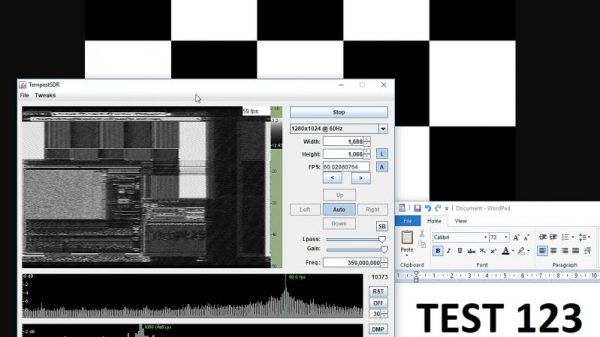
If the term TEMPEST sounds familiar, it’s because we’ve covered it before. [Elliot Williams] gave an introduction to the many modalities that fall under the TEMPEST umbrella, the US National Security Agency’s catch-all codename for bridging air gaps by monitoring the unintended RF, light, or even audio emissions of computers. And more recently, [Brian Benchoff] discussed a TEMPEST hack that avoided the need for thousands of dollars of RF gear, reducing the rig down to an SDR dongle and a simple antenna. There’s even an app for that now: TempestSDR, a multiplatform Java app that lets you screen scrape a monitor based on its RF signature. Trouble is, getting the app running on Windows machines has been a challenge, but RTL-SDR.com reader [flatfishfly] solved some of the major problems and kindly shared the magic. The video below shows TempestSDR results; it’s clear that high-contrast images at easiest to snoop on, but it shows that a $20 dongle and some open-source software can bridge an air gap. Makes you wonder what’s possible with deeper pockets.
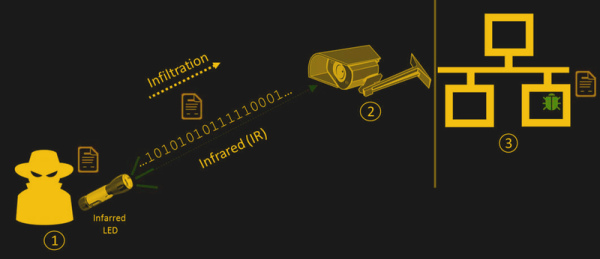
RF sniffing is only one of many ways to exfiltrate data from an air-gapped system. From power cords to security cameras, there seems to be no end to the ways to breach systems.