Another week of ransomware, and this time it’s the beef market that’s been shut down, due to a crippling infrastructure attack out of Russia — but hold up, it’s not that simple. Let’s cover the facts. Some time on Sunday, May 30, JBS USA discovered a ransomware attack against their systems. It seems that their response team did exceptionally well, pulling the plug on affected machines, and starting recovery right away. By Wednesday, it was reported that most of their operations were back in action.
Continue reading “This Week In Security: Ransomware, WeLock, And Amazon Arbitration”
Making A Dash Button Update Your To-do List
Amazon’s Dash Buttons are useful little devices, that let you automatically order a wide variety of common household goods at the press of a button. They’re cheap and wireless and readily available, and that makes them ripe for hacking. In just this vein, [Inbar] and [Ezra] found a way to make the Dash buttons update their to-do list.
[Inbar] uses Any.do to manage his to-do list. There’s no public API, but the service can be configured to respond to Alexa commands. Naturally, this meant that if a Dash Button could be configured to trigger a voice command, Alexa would then make the necessary additions to the list.
This was achieved with lashings of Python, a Raspberry Pi, and Apple’s text-to-speech engine. The Raspberry Pi is set up as a wireless hotspot, to which the Dash Buttons are connected. When the button is pressed, a DHCP request goes out as the button tries to phone home. By scraping the MAC address from this request, the Raspberry Pi can identify which button has been pressed, and then plays a recorded voice sample of Apple’s Samantha voice. This voice was specifically chosen to be the one most reliably understood by Alexa, which is responsible for parsing the voice command and updating the list on Any.do.
It’s a cheeky hack that doesn’t bother itself with the nitty-gritty of interfacing with various services and tools. Instead, it laces up a bunch of easy-to-use software and hardware, and gets the job done just as well.
As we’ve seen, Amazon’s Dash Button has been thoroughly pwned. Video after the break. Continue reading “Making A Dash Button Update Your To-do List”
Dash With Arduino
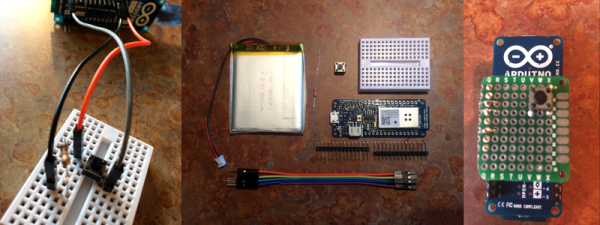
Amazon Dash is a handy service, and when Amazon released their AWS IoT platform, [Brian Carbonette] felt that it left out all the hardware hackers from the tinkering fun. Seeking justice, he put together a guide for an Arduino Dash button aimed at hardware hackers and those who are still easing into the world.
For his build, [Carbonette] used an Arduino MKR1000, laying out a few different configuration options for building your button. He has also gone to great lengths to help all comers tackle the Arduino-Dash API communication process by building an AmazonDRS Arduino Library, which handles all the “boring details,” so you can focus on the hardware. With the warning that the software-side setup is tedious the first time around, [Carbonette] has included a detailed manual for setting up the aforementioned AmazonDRS library, some example code, and a breakdown thereof. He also suggests implementing other features — such as a notification if the item is out of stock on Amazon — to tie the project together.
1btn – An Open Source Dash
The availability of cheap radios, omni-present WiFi and powerful web services means the IoT wave is here to stay. Amazon got into the act with its “do only one thing” Dash button. But a more interesting solution would be an IoT “do it all” button.
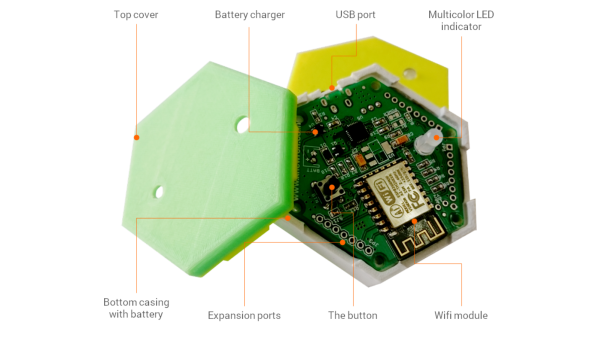
[Anand] has been working on his 1btn Open Source WiFi connected IoT button for a while. It connects to the Internet over WiFi to trigger whatever action you have assigned to it using a simple, online interface. It’s reconfigurable and open source. Which means it can be used in pretty imaginative ways, and if needed, can be re-flashed with your own custom firmware should you decide to really get under its hood.
The 1btn’s ESP8266 module is usually in sleep mode, waking up when the button is pressed, making the connection, performing the task and then going back to sleep once confirmation is received. A Red/Green LED indicates if the action was successful or not. You can set it up to send e-mails, messages, tweets or perform actions via a custom script, API or the IFTTT – maker channel. To make it hacker friendly, all of the ESP8266 GPIO pins are accessible via headers. This makes it convenient to add external sensors, for example. There’s also a (unpopulated) QFN footprint to allow adding an ATmega device (168P/328P) whose GPIO pins are also accessible via headers. This opens up a large number of additional applications for the device such as home automation.
On the software side, the 1btn connects to a web console, where you can set up an account, configure the device, register its MAC ID, assign it an alias and set up its actions. All of the source files for the 1btn – firmware, enclosure, schematic, BOM, PCB layout and example use cases – are posted on his Github repository.
Google’s OnHub Goes Toe To Toe With Amazon Echo
Yesterday Google announced preorders for a new device called OnHub. Their marketing, and most of the coverage I’ve seen so far, touts OnHub as a better WiFi router than you are used to including improved signal, ease of setup, and a better system to get your friends onto your AP (using the ultrasonic communication technique we’ve also seen on the Amazon Dash buttons). Why would Google care about this? I don’t think they do, at least not enough to develop and manufacture a $199.99 cylindrical monolith. Nope, this is all about the Internet of Things, as much as it pains me to use the term.
 OnHub boasts an array of “smart antennas” connected to its various radios. It has the 2.4 and 5 Gigahertz WiFi bands in all the flavors you would expect. The specs also show an AUX Wireless for 802.11 whose purpose is not entirely clear to me but may be the network congestion sensing built into the system (leave a comment if you think otherwise). Rounding out the communications array is support for ZigBee and Bluetooth 4.0.
OnHub boasts an array of “smart antennas” connected to its various radios. It has the 2.4 and 5 Gigahertz WiFi bands in all the flavors you would expect. The specs also show an AUX Wireless for 802.11 whose purpose is not entirely clear to me but may be the network congestion sensing built into the system (leave a comment if you think otherwise). Rounding out the communications array is support for ZigBee and Bluetooth 4.0.
I have long looked at Google’s acquisition of Nest and assumed that at some point Nest would become the Router for your Internet of Things, collecting data from your exercise equipment and bathroom scale which would then be sold to your health insurance provider so they may adjust your rates. I know, that’s a juicy piece of Orwellian hyperbole but it gets the point across rather quickly. The OnHub is a much more eloquent attempt at the same thing. Some people were turned off by the Nest because it “watches” you to learn your heating preferences. The same issue has arisen with the Amazon Echo which is “always listening”.
Google has foregone those built-in futuristic features and chosen a device to which almost everyone has already grown accustom: the WiFi router. They promise better WiFi and I’m sure it will deliver. What’s the average age of a home WiFi AP at this point anyway? Any new hardware would be an improvement. Oh, and when you start buying those smart bulbs, fridges, bathroom scales, egg trays, and whatever else it’ll work for them as well.
As far as hacking and home automation, it’s hard to beat the voice-activated commands we’ve seen with Echo lately, like forcing it to control Nest or operate your Roku. Who wants to bet that we’ll see a Google-Now based IoT standalone device quickly following the shipment of OnHub?
Continue reading “Google’s OnHub Goes Toe To Toe With Amazon Echo”
This Week In Security: LogoFail, National DNS Poison, And DNA
When there’s a vulnerability in a system library, we install updates, and go on with our lives. When there’s a vulnerability in a Java library, jars get rebuilt, and fixed builds slowly roll out. But what happens when there’s a vulnerability in a library used in firmware builds? And to make it even more fun, it’s not just a single vulnerability. All three major firmware vendors have problems when processing malicious images. And LogoFail isn’t limited to x86, either. UEFI Arm devices are vulnerable, too.
Continue reading “This Week In Security: LogoFail, National DNS Poison, And DNA”
Hackaday Podcast 030: Seven Years Of RTL-SDR, 3D Printing Optimized For The Eye, Sega Audiophile, Swimming In Brighteners
Hackaday Editors Mike Szczys and Elliot Williams curate the awesome hacks from the past week. On this episode, we marvel about the legacy RTL-SDR has had on the software-defined radio scene, turn a critical ear to 16-bit console audio hardware, watch generative algorithms make 3D prints beautiful, and discover why printer paper is so very, very bright white.
Take a look at the links below if you want to follow along, and as always tell us what you think about this episode in the comments!
Take a look at the links below if you want to follow along, and as always, tell us what you think about this episode in the comments!
Direct download (60 MB or so.)