Tabbed browsing was a gamechanger, allowing users to effectively browse multiple websites at once without losing context. It proved a better solution than using multiple windows, and was an efficiency boon celebrated by all. Many of us are tab fiends, opening great numbers at a time as a habitual part of our workflow. [Linus] decided to find out just how many he could open on a system armed with a full 2TB of RAM.
As may be obvious, setting up a system with 2TB of RAM is no mean feat. Special server-grade RAM modules were sourced, packing 128GB of RAM each, set up for ECC operation. Packing out 16 slots, there’s a performance penalty to addressing so much RAM with a single CPU, but for memory-intensive work, it’s worthwhile. The CPU in question is an AMD 64-core processor, providing plenty of grunt for the task at hand.
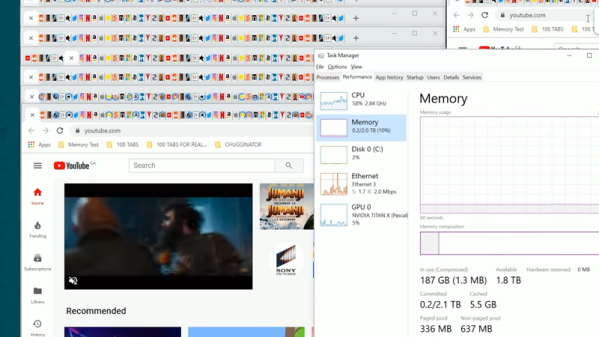
In testing, the machine began to slow down long before the RAM was full. Beyond 5000 tabs, things began to crawl. At 6000 tabs, it was simply impractical to open more, with the machine taking a full 26 seconds to respond to a single click. Memory usage at this point was just 200GB, suggesting that software limitations were getting in the way of opening yet more tabs.
While it’s not a useful measure of anything important, it’s fun to explore the limits nonetheless. We’ve seen their projects before, such as this original Xbox casemod. Video after the break.
Continue reading “Maxing Out Browser Tabs With 2TB Of Memory”

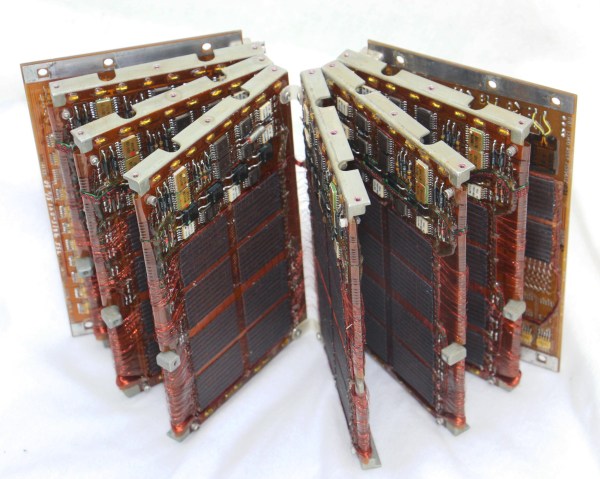
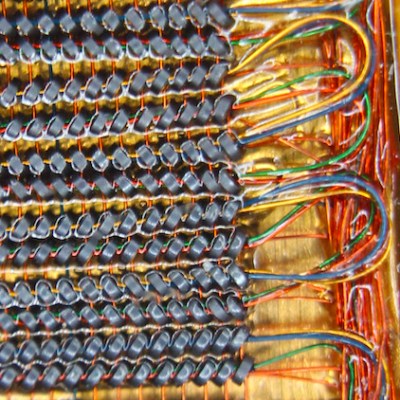 Amazingly these computers were composed of all digital logic, no centralized controller chip in this baby. That explains the need for the seven circuit boards which host a legion of logic chips, all slotting into a backplane.
Amazingly these computers were composed of all digital logic, no centralized controller chip in this baby. That explains the need for the seven circuit boards which host a legion of logic chips, all slotting into a backplane.