One of the major perks of all the affordable flight controllers and motors available from the hobby market is that you can really experiment with some crazy aircraft designs. [amazingdiyprojects] is experimenting with a coaxial helicopter design, with the goal off possibly using for a manned version in the future. (Video link, embedded below.)
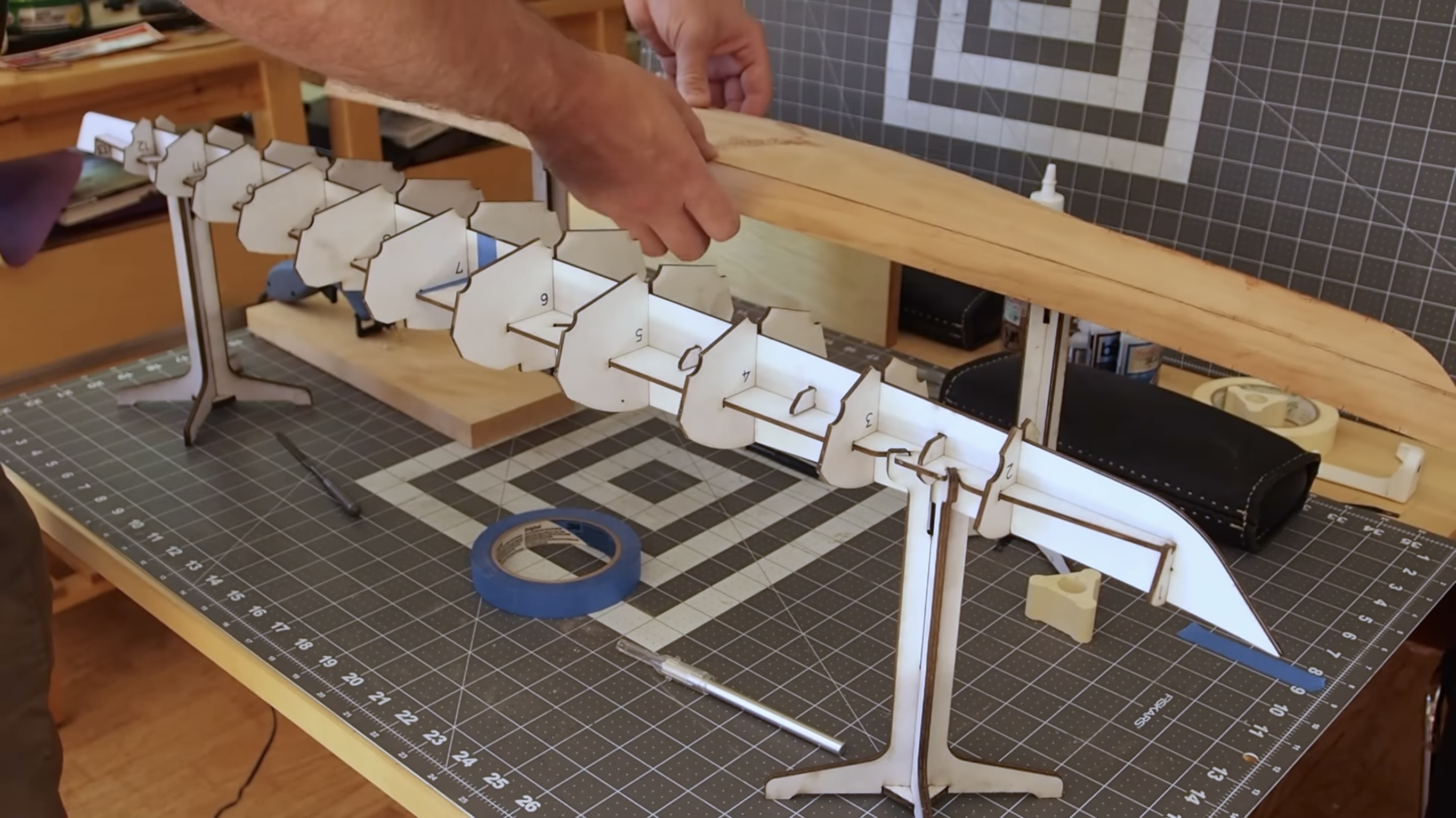
The aircraft uses a pair of coaxial counter-rotating motors with large propellers, with several redundant control surfaces below the propellers. One of the theoretical advantages of this arrangement, compared to the more conventional quadcopter type designs, is redundancy. While a quadcopter will start tumbling when a single motor fails, this design will still be able to descend safely with just one motor.
It is also not dependent on the main motors for yaw, pitch and roll control. In multirotors, the motors need to keep a significant amount of the motor’s available power in reserve to increase torque at a moment’s notice for attitude control. This craft can use all the available thrust from the motors for lift, since control is provided by the control surfaces. There are five sets of redundant control surfaces below the propellers, each set connected to a separate flight controller.
Another advantage of this design is efficient for a given footprint, since one large propeller will always be more efficient than multiple smaller propellers. One of the goals for [amazingdiyprojects] is to fit the full size craft in a shipping container or on a trailer for transport without dissasembly.
[amazingdiyprojects] has built manned drones before, using both electric motors and internal combustion engines. And don’t miss the most gonzo wind tunnel ever at 7:00 in the video below. Continue reading “Coaxcopter To Carry Man”