The small city of Naka (pop. 53K), a two-hour train ride from Tokyo on the eastern coast of Japan, was thrust into the international spotlight in the early dawn of Friday morning. A fire broke out among electroplating equipment in Renesas’s 300 nm N3 fabrication facility. It was extinguished before breakfast time, and fortunately nobody was injured nor were there any toxic chemical leaks. Only six hundred square meters on the first floor of the plant was damaged, but the entire building has to be closed for repairs. It will take approximately one month to restore normal operations, and CEO Hidetoshi Shibata is “concerned that there will be a massive impact on chip supplies”.
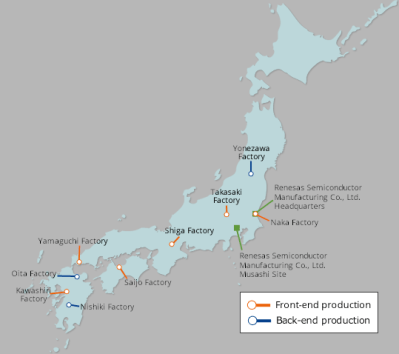
In a press conference on Sunday afternoon, Renesas reports that the source of the fire has been determined, but the details are still unclear:
The casing of the equipment and the plating tank have relatively low resistance to heat, and the equipment ignited due to overcurrent. However, the cause of the overcurrent and the reason for the ignition is currently being investigated.
Semiconductors are already in short supply, as we reported back in January, forcing slowdowns at many auto manufacturers. The Naka plant primarily makes automotive semiconductors, worsening an already stressed supply chain. While the news focuses on the automotive sector, this shortage spills over into many other industries as well.
Continue reading “Fire At Renesas Plant Fuels Chip Supply Woes”