Researchers from VUSec found a way to break ASLR via an MMU sidechannel attack that even works in JavaScript. Does this matter? Yes, it matters. A lot. The discovery of this security flaw along with the practical implementation is really important mainly because of two factors: what it means for ASLR to be broken and how the MMU sidechannel attack works inside the processor.
Address Space Layout Randomization or ASLR is an important defense mechanism that can mitigate known and, most importantly, unknown security flaws. ASLR makes it harder for a malicious program to compromise a system by, as the name implies, randomizing the process addresses when the main program is launched. This means that it is unlikely to reliably jump to a particular exploited function in memory or some piece of shellcode planted by an attacker.
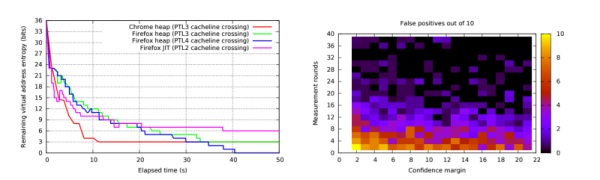
Breaking ASLR is a huge step towards simplifying an exploit and making it more reliable. Being able to do it from within JavaScript means that an exploit using this technique can defeat web browser ASLR protection running JavaScript, the most common configuration for Internet users.
ASLR have been broken before in some particular scenarios but this new attack highlights a more profound problem. Since it exploits the way that the memory management unit (MMU) of modern processors uses the cache hierarchy of the processor in order to improve the performance of page table walks, this means that the flaw is in the hardware itself, not the software that is running. There are some steps that the software vendors can take to try to mitigate this issue but a full and proper fix will mean replacing or upgrading hardware itself.
In their paper, researchers reached a dramatic conclusion:
Continue reading “ASLR^CACHE Attack Defeats Address Space Layout Randomization”