[MusashiAharon’s] dorm room door was practically begging to be hacked. There was already an electronic strike plate in place as well as junction boxes on the inside and out that were connected by conduit. Jumping on the bandwagon after seeing some other door lock hacks here, he built one that uses a rhythmic combination.
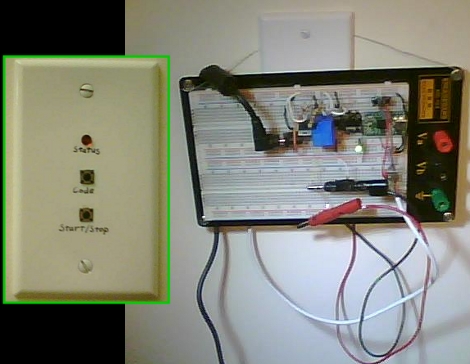
The control panel on the outside is a blank faceplate with two buttons and a status LED. Theses are wired to a jack and connected with a cable traveling through the conduit to a breadboard on the inside of the door. Seeing a large breadboard hanging on an outlet cover is a bit comical but it does the job. From there, a Teensy microcontroller waits for the code and if correct, actuates the strike plate via a relay.
The rhythmic nature of this lock reminds us of the knock-based system. One button signals the start and end of the code, the other is used to input the rhythmic sequence. This does seem a little more discreet and we’d imagine it’s quite hard to eavesdrop on the correct combination.