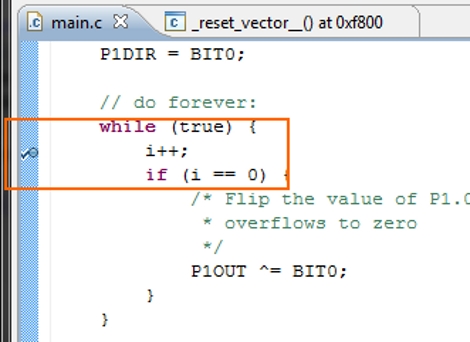
[Springuin] just posted a tutorial about debugging MSP430 projects using Eclipse. He read our feature about debugging under IAR, a proprietary IDE which TI offers as a code-limited freebie with the TI Launchpad. In that writeup we wondered if anyone would put together a tutorial using open source tools like DDD and GDB to make debugging easier for those that choose to use operating systems other than Windows. Even though he didn’t directly use those particular packages, this should work just as well.
Eclipse is a popular IDE for many different languages like C, C++, Java, and others. We’ve already seen it used to develop for the TI Evalbot on Linux systems. [Springuin] is using the Java-based IDE on a Windows system, and this is the first time we recall seeing directions on using an open-source alternative for programming with the TI Launchpad under Windows. That being said, the only real Windows specific parts are the steps necessary for communicating with the programmer. Since this method uses MSP-GCC and msp430-gdbproxy, it should be easy to do this under Linux as well. Use our tutorial to set up those tools if you haven’t already, then follow this one for a setting up and debugging in the Eclipse environment.