
Reader [Adrian] picked up a couple cheap wireless flash triggers on eBay. Unfortunately, his Sigma EF-500 DG Super strobe doesn’t have the necessary sync port to make use of these. He popped the device open to try to figure out a way to trigger the device manually. The first idea was to use the test button to fire the device. Thanks to lag, it didn’t work for anything under 1/20th. The solution was to go straight for the optical trigger. [Adrian] has posted some teardown pictures that will help you determine the appropriate solder points for your own mod. The only bit that’s left is adding a 3.5mm mono headphone jack as a sync port. He also has a post on modifying the flash for greater head movement.
flash126 Articles
Art From Code: Generative Graphics

[Keith Peters]’ blog Art From Code is devoted to his beautiful graphics from computer source code, also known as generative art. Although [Peters] is reluctant to reveal his source code, algorithmic graphics can be created with the help of tools like ActionScript, Flash, and Flex. There are some great tutorials that can start you on the path to making your own evocative art.
[via Neatorama]
IPhone Screengrab Issues

This is unfortunately another story we missed out on while we were trying to keep things from burning down. We told you that [Jonathan Zdziarski] was going to demonstrate iPhone lock code bypassing in a webcast. The real surprise came when he pointed out that the iPhone takes a screenshot every time you use the home button. It does this so it can do the scaling animation. The image files are presumably deleted immediately, but as we’ve seen before it’s nearly impossible to guarantee deletion on a solid state device. There’s currently no way to disable this behavior. So, even privacy conscious people have no way to prevent their iPhone from filling up storage with screenshots of all their text message, email, and browsing activities. Hopefully Apple will address this problem just like they did with the previous secure erase issue. O’Reilly promises to publish the full webcast soon.
[via Gizmodo]
Domestic Spying Brought To You By A Snuggly Bear

Mark Fiore’s Snuggly the Security Bear’s latest cartoon explains the wonders of constitutional compromise and how it helps prevent terrorism through domestic spying.
Related: Judge: FISA trumps state secrets, binds executive branch
[via EFF]
Gaming With Real-world Data
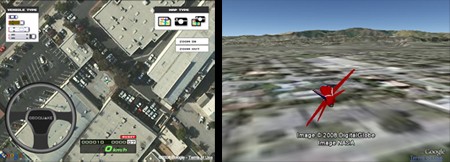
We were pretty excited by the prospect of location-aware software and its ability to pull map data into its functions, but what do you get when build software on top of a map-based service? Well, one possibility is 2D gaming on real maps.
Wii Dual NAND Flash Hack
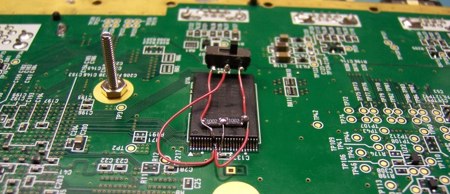
[ChipD] successfully installed two NAND flash chips into his Wii. He can keep the stock firmware on one and then flip a switch if he wants to boot using the other chip with a modified firmware. This hack is fairly straight forward. All it took was someone with steady hands to try it out. The new NAND chip is identical to the original and was salvaged from a flash drive. The chips were soldered as a stack except for the chip enable pin. The chip enable from each chip is attached to a small switch to toggle between which is active. You could use a TSOP socket to swap the different chips, but it wouldn’t fit inside the Wii case. This little switch could be hidden easily next to the GameCube ports.
Erase An IPhone Properly

A fundamental problem with flash memory has just gone mainstream. A detective successfully recovered data from a refurbished iPhone purchased from Apple. Flash memory controllers write to blocks randomly so using standard secure erase techniques are no guarantee that all of the storage space will be written.
[Rich Mogull] has posted a method that should wipe out almost all remnants of your personal data. You start by restoring the iPhone in iTunes and turning off all the syncing options. Next you create 3 playlists large enough to consume all of the phone’s storage space. Sync each playlist in turn and your residual personal data should be obliterated. All that’s left to do is sit back and wonder when the first article about the MacBook Air SSD being impossible to securely erase will be published…










