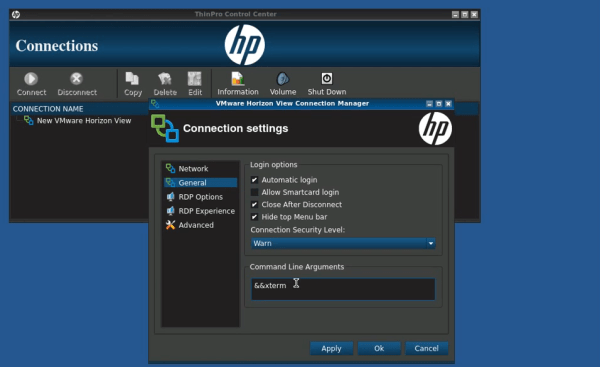
Sometimes hacks don’t have to be innovative to be satisfying. We thought that [daffy]’s instructions and video (embedded below the break) for turning an old WRT54G router into an Internet radio were worth a look even if he’s following a well-traveled path and one that we’ve reported on way back when.
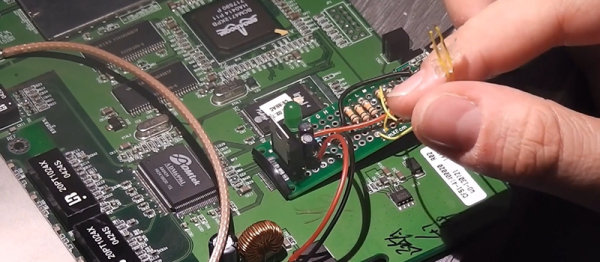
The hack itself is simple. [daffy] locates unused USB data lines, adds in a 5V voltage regulator to supply USB bus power, and then connects it all to a USB sound card. Hardware side, done! And while he doesn’t cover the software side of things in this first video, we know where he’s headed.
The WRT54G router was the first commodity Linux-based router to be extensively hacked, and have open-source firmware written for it. If you’re using OpenWRT or dd-wrt on any of your devices, you owe a debt to the early rootability of the WRT54G. Anyway, it’s a good bet that [daffy] is going to find software support for his USB sound card, but we remain in suspense to see just exactly how the details pan out.
Our favorite WRT54G hack is still an oldie: turning a WRT54G into the brains for a robot. But that was eight years ago now, so surely there’s something newer and shinier. What’s the coolest device that you’ve seen a WRT router hacked into?

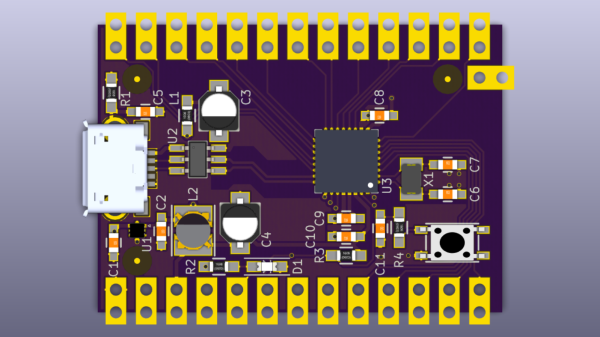
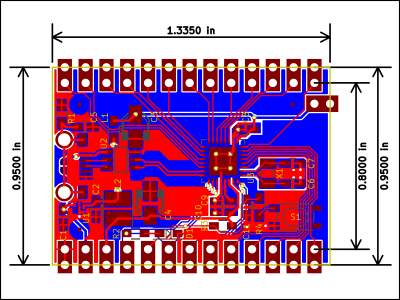 draw the schematic and layout. Using the
draw the schematic and layout. Using the