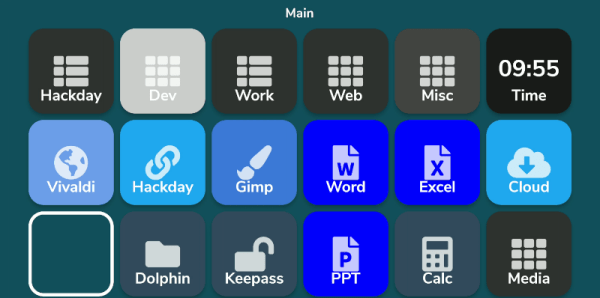
What do you do with those old Android or iPhone phones and tablets? You have plenty of options, but it is pretty easy to build your own stream deck with a little off-the-shelf software. What’s a stream deck, you ask? The name comes from its use as a controller for a live-streaming setup, but essentially, it’s an LCD touchscreen that can trigger things on your computer.
The software I’m using, Deckboard, is a server for Windows or Linux and, of course, an Android app. The app is free with some limitations, but for under $4 you can buy the full version. However, even the free version is pretty capable. You can use an Android phone or tablet and you can connect to the PC with a USB cable or WiFi. I’ve found that even with WiFi, it is handy to keep the phone charged, so realistically you are going to have a cable, but it doesn’t necessarily have to connect to the host computer.
Linux Setup
Setup is very easy. The biggest hurdle is you might need to set up your firewall to allow the server to listen on port 8500 with TCP. There are a few small issues when installing with Linux that you might want to watch out for. There are 32-bit and 64-bit versions in deb, tar.gz, and appimage format. There’s also a snap. The problem with the snap is it is sandboxed, so without effort you can’t easily launch programs, which is kinda the entire point. I finally removed it and installed the deb file which was fine.
There were still two other wrinkles. First, while Deckboard offers a way to launch programs, it must be a program from a list it reads from your system. That would be acceptable, but the list wasn’t complete. I never did figure out why some things show up on the list and others don’t. For example, GIMP which shows up on my application menu was absent. Yet other things that were fairly obscure did show up.
I thought this might be a dealbreaker until I found that Deckboard has a well-developed plugin system and one of those plugins lets you run an arbitrary command line. I guess it is a little less convenient, but it is much more flexible since you can launch any program you want and provide options to it as well.
The only other complaint I had is that when you run the program, it shows its configuration interface and puts itself in the system tray. That’s great the first time you run it, but on system startup, it would be nice to just have it quietly start. If there’s an option for that I haven’t found it. I’ll tell you how I solved that later, but, for now, just live with it.
Continue reading “Quick Hack: The Phone To Stream Deck Conversion” →