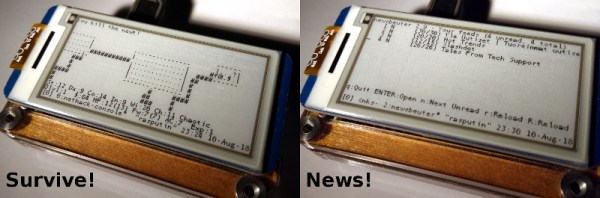
If you haven’t kept up with the world of e-ink displays, here’s some good news: they are pretty cheap now. For as little as $15 you can get a small e-ink display that has good enough performance and contrast to actually do something useful. There’s only one problem: figuring out how to drive them in your project.
Tired of seeing nothing but wiring diagrams and sample code when it came to actually putting these e-ink modules to use, [Jouko Strömmer] decided to try his hand at creating a turn-key application for these gorgeous little displays. The result is PaperTTY, a Python program that allows the user to open up a fully functional Linux virtual terminal on an e-ink display.
 Of course, there are some caveats. For one, this all assumes you’re using a Waveshare display (specifically their 2.13 inch HAT) connected to a Raspberry Pi over SPI. Not to say that’s the only hardware combination that will work, but it’s the only one that [Jouko] has done any testing on at this point. If you want to try to shake things up in terms of hardware, you might need to get your hands dirty.
Of course, there are some caveats. For one, this all assumes you’re using a Waveshare display (specifically their 2.13 inch HAT) connected to a Raspberry Pi over SPI. Not to say that’s the only hardware combination that will work, but it’s the only one that [Jouko] has done any testing on at this point. If you want to try to shake things up in terms of hardware, you might need to get your hands dirty.
The advantage of being able to open a Linux VT on one of these e-ink displays is pretty simple: you can run basically any piece of software you want on it. Rather than having to come up with software that specifically features support for the display, you can just use (or write) standard Linux console programs. [Jouko] mentions a number of popular programs such as vim and irssi, but you could just as easily write a Bash script to dump whatever data you like to the screen.
In the video after the break [Jouko] shows PaperTTY in action for the doubters who think these sorts of displays are no good for interactive use. The display is very crisp and readable, with no signs of flickering. Overall he says the experience is not unlike using a slow SSH connection. It might not be how we’d like to use a computer full time, but we can definitely see the potential.
With the recent progress with Kindle hacking, it seems that interest in e-ink is as high as ever. Despite what the haters might claim, it’s a useful niche tech that still holds plenty of promise.
Continue reading “Run A Linux Terminal On Cheap E-Ink Displays”


 Over the years, a number of gadgets with BLE have popped up such as the LightBlue Bean, BLE Beacons as well as quadcopters like the FlexBot that rely on BLE for communication. Android or iOS apps are the predominant method of talking to these wonderful gadgets though there are alternatives.
Over the years, a number of gadgets with BLE have popped up such as the LightBlue Bean, BLE Beacons as well as quadcopters like the FlexBot that rely on BLE for communication. Android or iOS apps are the predominant method of talking to these wonderful gadgets though there are alternatives.