There was a period in the late 1980s when the home computer to own did not come with an Apple logo and was not an IBM, Compaq, or any of the other clones, but instead sported a Commodore logo. The Amiga 500 was an all-in-one console-style cased machine that maybe wasn’t quite the computing powerhouse you might have wished it to be, but gave you enough of the capabilities of the more accomplished 16-bit machines of the day to be an object of desire while also having a games catalogue second to none.
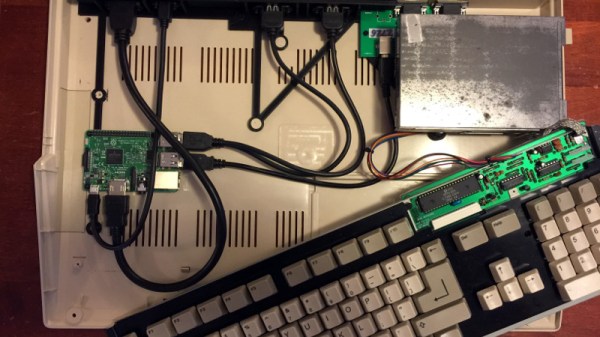
A500s have survived in reasonable numbers, but inevitably working A500s haven’t. Fortunately there are decent emulators, and it was for one of these that [intric8] has produced an extremely well-done installation of a Raspberry Pi 3 in an Amiga case. The intention has been throughout to avoid modification or damage to the Amiga case, and eventually to have all Amiga internal peripherals including the floppy drive in a fully working condition.
The result has a Tynemouth Software USB adaptor for the Amiga keyboard, and a set of nicely designed 3D printed backplates to bring the extended Raspberry Pi ports to the back of the case. The floppy isn’t yet interfaced and there isn’t a socket for the quadrature mouse, but otherwise it’s a very tidy build. He might be interested in one of the several USB to quadrature interfaces we’ve featured over the years.
You might ask why so much effort should be put in for an emulation of an A500, and in a sense you’d be right to do so. The Pi will run the emulator from any case or none. But if you happen to have a spare A500 case, why not give this one a go!