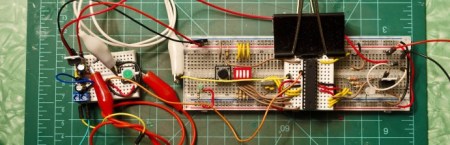
[Ben Krasnow] built his own version of the TSA’s body scanner. The device works by firing a beam of x-rays at at target. Some of the beam will go through the target, some will be absorbed by the target, and some will reflect back. These reflected x-rays are called ‘backscatter‘, and they are captured to create an image.
In [Ben]’s setup a rotating disk focuses x-rays into beams that travel in arcs across the X-axis. The disk is moved along the Y-axis to fill in the scan. On the disk assembly, there is a potentometer to measure the y-axis position of the beam, and an optical sensor to trigger an oscilloscope, aligning the left and right sides of the image. Using these two sensors, the scope can reconstruct an X-Y plot of the scan.
To detect the x-rays, a phosphorous screen turns the backscattered x-rays into visible light, and a photo-multiplier amplifies the light source. A simple amplifier circuit connects the photo-multiplier to a scope, controlling the brightness at each point.
The result is very similar to the TSA version, and [Ben] managed to learn a lot about the system from a patent. This isn’t the first body scanner we’ve seen though: [Jeri Ellsworth] built a microwave version a couple years ago.
The impressive build does a great job of teaching the fundamentals of backscatter imaging. [Ben] will be talking about the project at EHSM, which you should check out if you’re in Berlin from December 28th to the 30th. After the break, watch [Ben]’s machine scan a turkey in a Christmas sweater.