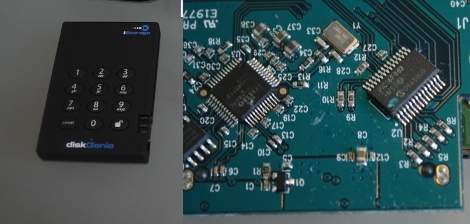
Our friend [Sprite_TM] took a look at the security of a code-protected hard disk. The iStorage diskGenie is an encrypted USB hard drive that has a keypad for passcode entry. After cracking it open he found that the chip handling the keypad is a PIC 16F883 microcontroller. He poked and prodded at the internals and found some interesting stuff. Like the fact that there is an onboard LED that blinks differently based on the code entered; one way for the right code, another for the wrong code of the right number of digits, and a third for a wrong code with the wrong number of digits. This signal could be patched into for a brute force attacking but there’s a faster way. The microcontroller checks for the correct code one digit at a time. So by measuring the response time of the chip an attacker can determine when the leading digit is correct, and reduce the time needed to crack the code. There is brute force protection that watches for multiple incorrect passwords but [Sprite_TM] even found a way around that. He attached an AVR chip to monitor the PIC response time. If it was taking longer than it should for a correct password the AVR resets the PIC before it can write incorrect attempt data to its EEPROM. This can be a slow process, but he concluded it should work. We had fun watching the Flash_Destroyer hammer away and we’d like to see a setup working to acquire the the code from this device.