If you’ve ever worked with FPGAs, you’ve dealt with the massive IDEs provided by the vendors. Xilinx’s ISE takes about 6 gigabytes, and Altera’s Quartus clocks in at over 10 gigs. That’s a lot of downloading proprietary software just to make an LED blink.
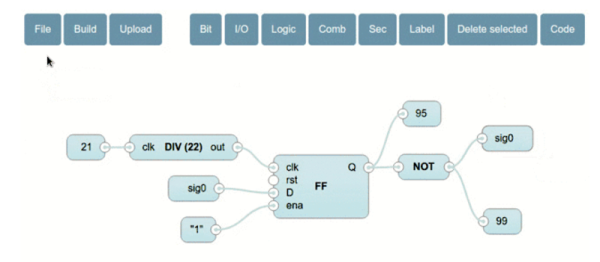
[Jesús Arroyo]’s Icestudio is a new, graphical tool that lets you generate Verilog code from block diagrams and run it on the Lattice Semi iCEstick development board. A drag and drop interface lets you connect IOs, logic gates, dividers, and other elements. Once your block diagram is ready, a single button press downloads the code to the iCEstick.
Under the hood, Icestudio uses IceStorm, which we’ve discussed on HaD in the past, including this great talk by [Clifford], Icestorm’s lead. For the GUI, Icestudio uses nw.js, which spits out JSON based on the block diagram. This JSON is converted into a Verilog file and a PCF file. The Verilog is used to create the logic on the FPGA, and the PCF is used to define the pin configuration for the device. Clicking on selected modules reveals the generated Verilog if you want to know what’s actually going on.
It’s experimental, but this looks like a neat way to get started on FPGAs without learning a new language or downloading many gigs of toolchains. We’re hoping Icestudio continues to grow into a useful tool for education and FPGA development. A demo follows after the break.
[Thanks to Nils for the tip!]
Continue reading “Icestudio: An Open Source Graphical FPGA Tool”