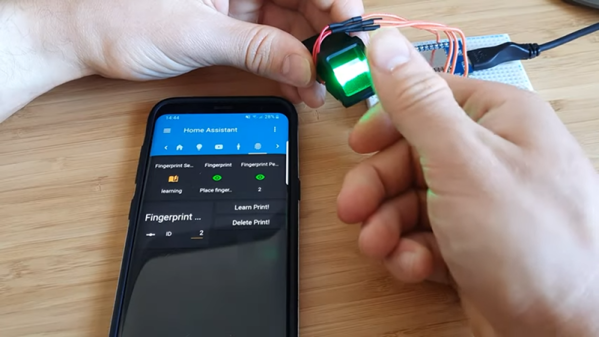
With his young son’s birthday coming up in a few weeks, [Mike Buss] wanted to build him something fun that the boy could hold on to all his life. After doing some sketching, [Mike] arrived at the idea to make a memory box uses a fingerprint scanner to show different pictures based on the fingerprint.
 [Mike] started by rendering the box in Blender and then cutting a sizable hole in the lid for the E-ink screen. That’s around the time the first problem came up — there were weird vertical lines in the display. Sure enough, that screen was broken. Then he added the SD card reader, but the SD card wouldn’t work, and was heating up besides. Finally, the fingerprint scanner was causing issues, but it turned out that the power supply was at fault.
[Mike] started by rendering the box in Blender and then cutting a sizable hole in the lid for the E-ink screen. That’s around the time the first problem came up — there were weird vertical lines in the display. Sure enough, that screen was broken. Then he added the SD card reader, but the SD card wouldn’t work, and was heating up besides. Finally, the fingerprint scanner was causing issues, but it turned out that the power supply was at fault.
After all of that, [Mike] switched from an ESP32 to a Raspi Zero W to simplify the whole process of finding a photo tagged with the person’s fingerprint. [Mike] added a Python script that listens for new memories over Wi-Fi. A memory in this case consists of a picture, a description, a list of people tagged in the picture, and some additional metadata.
One important lesson [Mike] learned was that of balancing planning vs. just taking action. If he had taken the time to consider the complexity of the tagged-photo retrieval system, he would have arrived at an SBC solution much sooner. Be sure to check out the build video after the break.
You can have all sorts of fun with fingerprint scanners, like this one that opens a secret bookcase door.
Continue reading “Memory Box Shows Photos Based On Fingerprint”




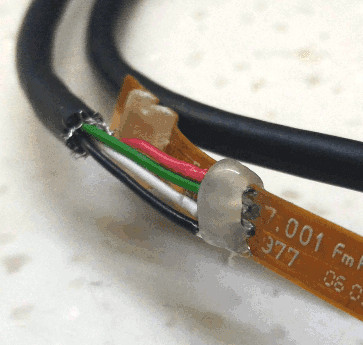




 He found a cheap replacement fingerprint scanner on hacker’s heaven, also known as eBay. It had four wires attached to a 16 pin connector. Investigation on the scanner end showed the outer pair were power and ground which made [Serge] suspect it was a USB device. Wiring up a USB connector and trying it the device was recognized but with a lot of errors. He swapped the signal lines and everything was perfect. He had sudo at his finger tip.
He found a cheap replacement fingerprint scanner on hacker’s heaven, also known as eBay. It had four wires attached to a 16 pin connector. Investigation on the scanner end showed the outer pair were power and ground which made [Serge] suspect it was a USB device. Wiring up a USB connector and trying it the device was recognized but with a lot of errors. He swapped the signal lines and everything was perfect. He had sudo at his finger tip.









