By now, most Windows users are set up with decently functional machines running Windows 10 or 11. Of course there are a few legacy machines still lagging behind on Windows 7 or 8 and plenty of computers in industrial settings running ancient proprietary software on Windows XP. But only the most hardcore of IBM PC users are still running DOS, and if you have eschewed things like Unix for this command-line operating system this long you might want to try using it to get online in the Fediverse with Mastodon.
The first step is getting DOS 6.22, the most recent version released in 1994, set up with all the drivers and software needed to access the Internet. At the time of its release there were many networking options so the operating system didn’t include these tools by default. [Stephen] first sets up an emulated NE2000-compatible networking card and then installs the entire TCP/IP stack and then gets his virtual machine set up with an IP address.
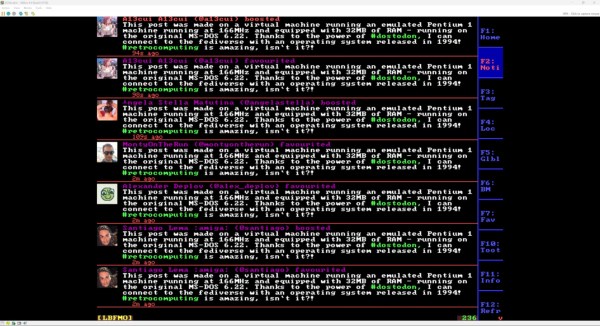
With a working Internet connection set up, the next step on the path of exploring federated social media is to install DOStodon (although we might have favored the name “MastoDOS”) which is a Mastodon client specifically built for MS-DOS by [SuperIlu]. There are pre-compiled packages available on its GitHub page for easy installation in DOS but the source code is available there as well. And, if this is your first time hearing about the Fediverse, it is mostly an alternative to centralized social media like Facebook and Reddit but the decentralization isn’t without its downsides.