Although quantum computing is still in its infancy, enough progress is being made for it to look a little more promising than other “revolutionary” technologies, like fusion power or flying cars. IBM, Intel, and Google all either operate or are producing double-digit qubit computers right now, and there are plans for even larger quantum computers in the future. With this amount of inertia, our quantum computing revolution seems almost certain.
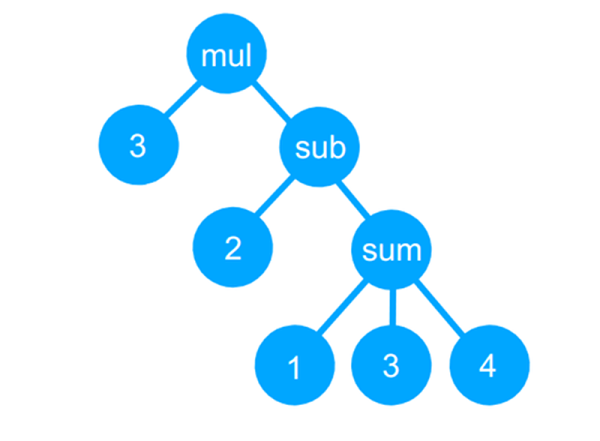
There’s still a lot of work to be done, though, before all of our encryption is rendered moot by these new devices. Since nothing is easy (or intuitive) at the quantum level, progress has been considerably slower than it was during the transistor revolution of the previous century. These computers work because of two phenomena: superposition and entanglement. A quantum bit, or qubit, works because unlike a transistor it can exist in multiple states at once, rather than just “zero” or “one”. These states are difficult to determine because in general a qubit is built using a single atom. Adding to the complexity, quantum computers must utilize quantum entanglement too, whereby a pair of particles are linked. This is the only way for any hardware to “observe” the state of the computer without affecting any qubits themselves. In fact, the observations often don’t yet have the highest accuracy themselves.
There are some other challenges with the hardware as well. All quantum computers that exist today must be cooled to a temperature very close to absolute zero in order to take advantage of superconductivity. Whether this is because of a reduction in thermal noise, as is the case with universal quantum computers based on ion traps or other technology, or because it is possible to take advantage of other interesting characteristics of superconductivity like the D-Wave computers do, all of them must be cooled to a critical temperature. A further challenge is that even at these low temperatures, the qubits still interact with each other and their read/write devices in unpredictable ways that get more unpredictable as the number of qubits scales up.
So, once the physics and the refrigeration are sorted out, let’s take a look at how a few of the quantum computing technologies actually manipulate these quantum curiosities to come up with working, programmable computers. Continue reading “Quantum Computing Hardware Teardown” →