Disk space is allocated in clusters of a certain size. When a file is written to disk and the file size is smaller than the cluster(s) allocated for it, there is an unused portion of varying size between the end of the file’s data and the end of the allocated clusters. This unused space is the slack space, it’s perfectly normal, and [Zachary Parish] had an idea to write a tool to hide data in it.
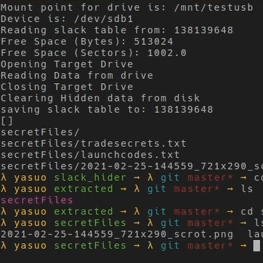
[Zachary]’s tool is in Python and can map available slack space and perform read and write operations on it, treating the disparate locations as a single unified whole in which to store arbitrary files. A little tar and gzip even helps makes things more efficient in the process.
There’s a whole demo implemented on Linux using a usb drive with some decoy files to maximize the slack space, and you can watch it in action in the video embedded below. It’s certainly more practical than hiding data in a podcast!
Note that this is just a demo of the concept. The approach does have potential for handling secret data, but [Zachary] points out that there are — from a serious data forensics point of view– a number of shortcomings in its current form. For example, the way the tool currently structures and handles data makes it quite obvious that something is going on in the slack space.
[Zachary] created this a few years ago and has some ideas about how to address those shortcomings and evolve the tool, so if you have ideas of your own or just want to try it out, the slack_hider GitHub repository is where you want to go.
Continue reading “Make A Secret File Stash In The Slack Space”



















