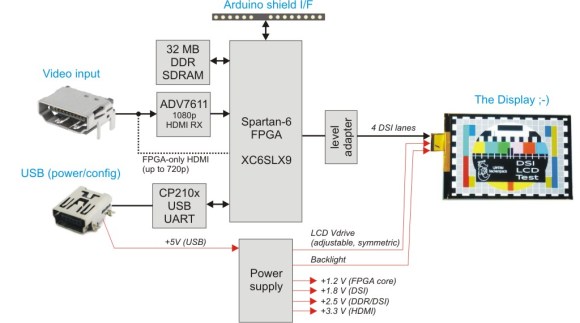
[Tomasz] tipped us about the well documented MIPI DSI Display Shield / HDMI Adapter he put on hackaday.io. The Display Serial Interface (DSI) is a high speed packet-based interface for delivering video data to recent LCD/OLED displays. It uses several differential data lanes which frequencies may reach 1 GHz depending on the resolution and frame rate required.
The board explained in the above diagram therefore allows any HDMI content to be played on the DSI-enabled scrap displays you may have lying around. It includes a 32MB DDR memory which serves as a frame buffer, so your “slow” Arduino platform may have enough time to upload the picture you want to display.
The CP2103 does the USB to UART conversion, allowing your computer to configure the display adapter internal settings. The platform is based around the XC6SLX9 Spartan-6 FPGA and all the source code may be downloaded from the official GitHub repository, along with the schematics and gerbers. After the break we’ve embedded a demonstration video in which a Raspi drives an iPhone 4 LCD.