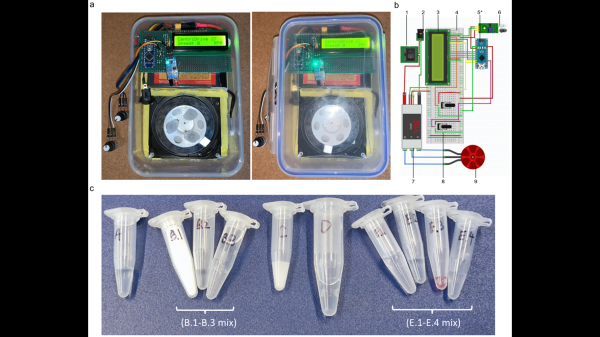
Throughout this two-year global COVID-19 nightmare, one thing that has been sorely lacking is access to testing. “Flu-like symptoms” covers a lot of ground, and knowing if a sore throat is just a sore throat or something more is important enough that we’ve collectively plowed billions into testing. Unfortunately, the testing infrastructure remains unevenly distributed, which is a problem this backpack SARS-CoV-2 testing lab aims to address.
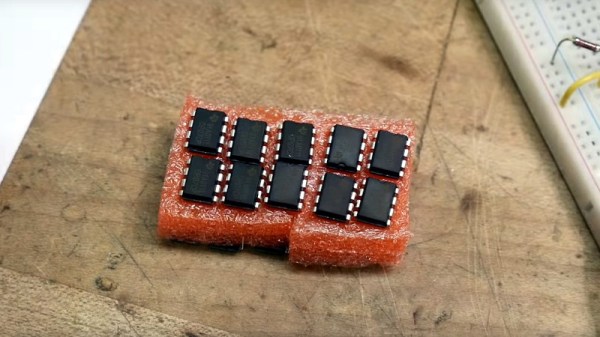
The portable lab, developed by [E. Emily Lin] and colleagues at the Queen Mary University of London, uses a technique called LAMP, for loop-mediated isothermal amplification. LAMP probably deserves an article of its own to explain the process, but suffice it to say that like PCR, LAMP amplifies nucleic acid sequences, but does so without the need for expensive thermal cycling equipment. The kit contains a microcentrifuge that’s fashioned from an e-waste hard drive, a 3D printed rotor, and an Arduino to drive the motor and control the speed. The centrifuge is designed to run on any 12 VDC source, meaning the lab can be powered by a car battery or solar panel if necessary. Readout relies on the trusty Mark I eyeball and a pH-indicating buffer that changes color depending on how much SARS-CoV-2 virus was in the sample.
Granted, the method used here still requires more skill to perform than a simple “spit on a stick” rapid antigen test, and it’s somewhat more subjective than the “gold standard” quantitative polymerase chain reaction (qPCR) assay. But the method is easily learned, and the kit’s portability, simple design, and low-cost construction could make it an important tool in attacking this pandemic, or the next one.
Thanks to [Christian Himmler] for the tip.