An adult human can produce about 100 Wh of mechanical power whilst cycling, which is a not inconsiderable amount if you can convert that to electricity with reasonable efficiency. In a recent article on EDN [T. K. Hareendran] goes over a few ways that you can turn the rotary motion of pedaling into usable electrical power.
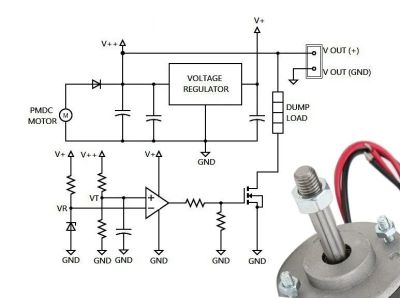
A basic form of this is already widely deployed, in the form of a bicycle dynamo that is used to supply power to the front and rear lights. These typically put out something like 3 watts at 6 VAC, so with a simple bridge rectifier and some smoothing this can power a pretty bright LED or two. To get more out of it, you need to use a more capable generator, which can also be a brushed or brushless DC motor in a pinch, with ideally a flywheel in the whole contraption to balance out variations in the human power input.
As for the potential here, a commercial solution like the K-Tor Power Box 50 is specified for ‘greater than’ 50 Watt, with a nominal 12 VDC output. Its target market is emergency generators, with enough capability to keep phones, radios and flashlights charged. Considering the $435 asking price, there is probably quite a lot of DIY potential well within that price bracket, especially if you already have many of the requisite parts lying around.
Fortunately this is not a new idea, with us having covered using bicycles as well as gym equipment to generate electricity in the past.