Last week the schedule for our weekly security column collided with the Independence Day holiday. The upside is that we get a two-for-one deal this week, as we’re covering two weeks worth of news, and there is a lot to cover!
[Petko Petrov], a security researcher in Bulgaria, was arrested last week for demonstrating an weakness he discovered in a local government website. In the demonstration video, he stated that he attempted to disclose the vulnerability to both the software vendor and the local government. When his warnings were ignored, he took to Facebook to inform the world of the problem.
From the video, it appears that a validation step was performed on the browser side, easily manipulated by the end user. Once such a flaw is discovered, it becomes trivial to automate the process of scraping data from the vulnerable site. The vulnerability found isn’t particularly interesting, though the amount of data exposed is rather worrying. The bigger story is that as of the latest reports, the local government still intends to prosecute [Petko] for downloading data as part of demonstrating the attack.
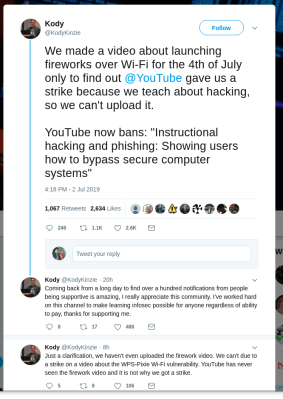
Youtube Censorship
In related news, Google has begun cracking down on “Instructional Hacking and Phishing” videos. [Kody] from the Null Byte Youtube channel found himself locked out of his own channel, after receiving a strike for a video discussing a Wifi vulnerability.
The key to getting a video unblocked seems to be generating lots of social media attention. Enough outcry seems to trigger a manual review of the video in question, and usually results in the strike being rescinded.
Improved Zip Bomb
A zip bomb is a small zip file that unzips into a ridiculously large file or collection of files. While there are obvious nefarious uses for such a file, it has also become something of a competition, crafting the most extreme zip bomb. The previous champion was 42.zip, a recursive zip file that when fully extracted, weighs in at 42 petabytes. A new contender may have just taken the crown, and without using zip file recursion.
[David Fifield] discovered a pair of ZIP tricks. First being that multiple files can be constructed from a single “kernel” of compressed data. The second is that file headers could also be part of files to be decompressed. It’s clever work, and much easier to understand when looking at the graphics he put together. From those two points, the only task left is to optimize. Taking advantage of the zip64 format, the final compression ratio was approximately 98 million to one.
Breaking OpenPGP Keyservers
OpenPGP as we know it is on the ropes. OpenPGP is the technique that allows encryption and verification of emails through cryptographic signatures. It’s the grandaddy of modern secure communication, and still widely used today. One of the features of OpenPGP is that anyone can upload their public key to keyservers hosted around the world. Because of the political climate in the early 90’s when OpenPGP was first developed, it was decided that a baked-in feature of the keyserver was that uploaded keys could never be deleted.
Another feature of OpenPGP keys is that one user can use their key to sign another user’s key, formally attesting that it is valid. This creates what is known as a “web of trust”. When an OpenPGP instance validates a signature, it also validates all the attestations attached to that signature. Someone has spammed a pair of OpenPGP certificates with tens of thousands of signatures. If your OpenPGP client refreshes those signatures, and attempts to check the validations, it will grind to a halt under the load. Loading the updated certificate permanently poisons the offline key-store. In some cases, just the single certificate can be deleted, but some users have had to delete their entire key store.
It’s now apparent that parts of the OpenPGP infrastructure hasn’t been well maintained for quite some time. [Robert J. Hansen] has been spearheading the public response to this attack, not to mention one of the users directly targeted. In a follow-up post, he alluded to the need to re-write the keyserver component of OpenPGP, and the lack of resources to do so.
It’s unclear what will become of the OpenPGP infrastructure. It’s likely that the old keyserver network will have to be abandoned entirely. An experimental keyserver is available at keys.openpgp.org that has removed the spammed signatures.
Beware the QR Codes
Link shorteners are a useful way to avoid typing out a long URL, but have a downside — you don’t know what URL you’re going to ahead of time. Thankfully there are link unshorteners, like unshorten.it. Paste a shortlink and get the full URL, so you don’t accidentally visit a shady website because you clicked on a shortened link. [Nick Guarino] over at cofense.com raises a new alarm: QR codes can similarly lead to malicious or questionable websites, and are less easily examined before scanning. His focus is primarily how a QR code can be used to bypass security products, in order to launch a fishing attack.
Most QR scanners have an option to automatically navigate to the web page in the code. Turn this option off. Not only could scanning a QR code lead to a malicious web site, but URLs can also launch actions in other apps. This potential problem of QR codes is very similar to the problem of shortened links — the actual payload isn’t human readable prior to interacting with it, when it’s potentially too late.
Dereferencing Pointers for Fun and Profit
On the 10th, the Eset blog, [welivesecurity], covered a Windows local priveledge escalation 0-day being actively exploited in the wild. The exploit highlights several concepts, one of which we haven’t covered before, namely how to use a null pointer dereference in an exploit.
In C, a pointer is simply a variable that holds a memory location. In that memory location can be a data structure, a string, or even a callable function. By convention, when pointers aren’t referring to anything, they are set to NULL. This is a useful way to quickly check whether a pointer is pointing to live data. The process of interacting with a pointer’s data is known a dereferencing the pointer. A NULL pointer dereference, then, is accessing the data referred to by a pointer that is set to NULL. This puts us in the dangerous territory of undefined behavior.
Different compilers, architectures, and even operating systems will potentially demonstrate different behavior when doing something undefined. In the case of C code on 32-bit Windows 7, NULL is indistinguishable from zero, and memory location zero is a perfectly valid location. In this case, we’re not talking about the physical location zero, but logical address zero. In modern systems, each process has a dedicated pool of memory, and the OS manages the offset and memory mapping, allowing the process to use the simpler logical memory addressing.
Windows 7 has a function, “NtAllocateVirtualMemory”, that allows a process to request access to arbitrary memory locations. If a NULL, or zero, is passed to this function as the memory location, the OS simply picks a location to allocate that memory. What many consider a bug is that this function will effectively round down small memory locations. It’s quite possible to allocate memory at logical address 0/NULL, but is considered to be bad behavior. The important takeaway here is that in Windows 7, a program can allocate memory at a location referred to by a null pointer.
On to the vulnerability! The malicious program sets up a popup menu and submenu as part of its GUI. While this menu is still being initialized, the malicious program cancels the request to set up the menu. By timing the cancellation request precisely, it’s possible for the submenu to still be created, but to be a null pointer instead of the expected object. A second process can then trigger the system process to call a function expected to be part of the object. Because Windows allows the allocation of memory page zero, this effectively hands system level execution to the attacker. The full write-up is worth the time to check out.
Zoom Your Way to Vulnerability
Zoom is a popular web-meeting application, aimed at corporations, with the primary selling point being how easy it is to join a meeting. Apparently they worked a bit too hard on easy meeting joins, as loading a malicious webpage on a Mac causes an automatic meeting join with the mic and webcam enabled, so long as that machine has previous connected to a Zoom meeting. You would think that uninstalling the Zoom client would be enough to stop the madness, but installing Zoom also installs a local webserver. Astonishingly, uninstalling Zoom doesn’t remove the webserver, but it was designed to perpetually listen for a new Zoom meeting attempt. If that sounds like a Trojan to you, you’re not wrong.
The outcry over Zoom’s official response was enough to inform them of the error of their ways. They have pushed an update that removes the hidden server and adds a user interaction before joining a meeting. Additionally, Apple has pushed an update that removes the hidden server if present, and prompts before joining a Zoom meeting.
Wireless Keyboards Letting You Down
Have you ever typed your password using a wireless keyboard, and wondered if you just broadcast it in the clear to anyone listening? In theory, wireless keyboards and mice use encryption to keep eavesdroppers out, but at least Logitech devices have a number of problems in their encryption scheme.
Part of the problem seems to be Logitech’s “Unifying” wireless system, and the emphasis on compatibility. One receiver can support multiple devices, which is helpful when eliminating cable clutter, but also weakens the encryption scheme. An attacker only has to be able to monitor the radio signals during pairing, or even monitoring signals while also observing keypresses. Either way, a few moments of processing, and an attacker has both read and write access to the wireless gear.
Several even more serious problems have fixed with firmware updates in the past years, but [Marcus Mengs], the researcher in question, discovered that newly purchased hardware still doesn’t contain the updated firmware. Worse yet, some of the effected devices don’t have an officially supported firmware update tool.
Maybe wired peripherals are the way to go, after all!