This project, sent in by [Henk], goes through a few different ways to make a solder stencil using a vinyl cutter, a CO2 laser, and a fiber laser.
The project starts with identifying a method to convert the board’s Gerber files to a PNG, which is ultimately used to create a vector file for use with the laser. The first stencil, made with the CO2 laser, was cut out of masking tape. This worked fine for larger cutouts and is certainly a cheap option if you don’t have too many small components. A slightly better approach with the CO2 laser was using vinyl sheet release paper, which seemed to hold together better than the tape.
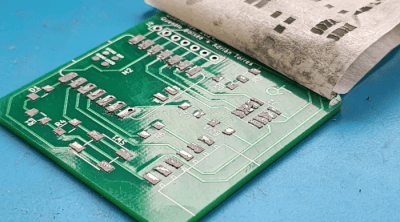
A vinyl cutter was also used as an experiment, but it didn’t perform as well as the CO2 laser, as expected, since the cutter uses a knife rather than light, leading to some tearing issues.
The final method utilized a fiber laser and an empty drink can to create a metal stencil. First, the can had to be cut open, heated, and flattened. The fiber laser was able to cut clean footprints in the aluminum, creating a stencil that would hold up to more use than the paper variations.
The finale of this exploration into laser stencil making was using the fiber laser to solder the board together. The stencil was used to spread paste on the pads, parts were placed on the board, and then the fiber laser heated the solder paste to solder them to the board. The board looked a bit toasty afterwards, but we imagine the process could be fine-tuned to reduce the collateral damage a bit.
Once you’ve got your stencil ready to go, you can combine it with a 3D printed jig to hold the PCB while you apply the solder paste.