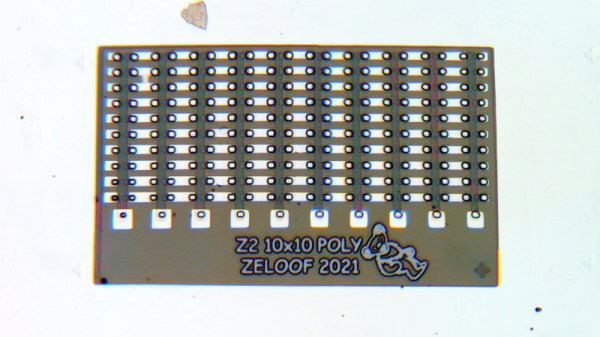
Back in 2018 we reported on the first silicon integrated circuit to be produced in a homemade chip fab. It was the work of [Sam Zeloof], and his Z1 chip was a modest six-transistor amplifier. Not one to rest on his laurels, he’s back with another chip, this time the Z2 is a hundred-transistor array. The Z2 occupies about a quarter of the area of the previous chip and uses a 10µm polysilicon gate process as opposed to the Z1’s metal gates. It won’t solve the global chip shortage, but this is a major step forward for anyone interested in building their own semiconductors.
The transistors themselves are FETs, and [Sam] is pleased with their consistency and characteristics. He’s not measured his yield on all samples, but of the twelve chips made he says he has one fully functional chip and a few others with at least 80% functionality. The surprise is that his process is less complex than one might expect, which he attributes to careful selection of a wafer pre-treated with the appropriate oxide layer.
You can see more about the Z2 in the video below the break. Meanwhile, should you wish to learn more about the Z1 you can see [Sam’s] Hackaday Superconference talk on the subject. We’re looking forward to the Z3 when it eventually arrives, with bated breath!
Continue reading “The Zeloof Z2 Intergrated Circuit Has 100 Transistors”