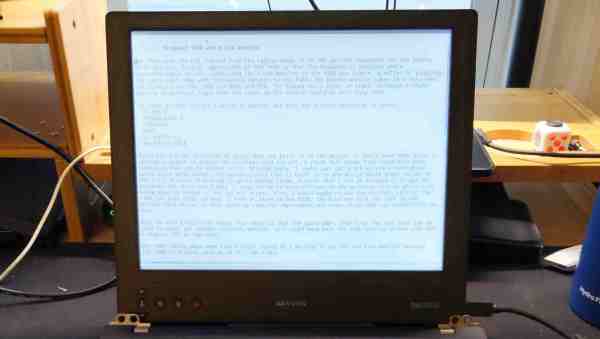
[Alexander Soto] prefers the reduced eye-strain of an e-ink display, but he doesn’t have a portable solution to use at different work stations. The solution? Make your own e-ink laptop. Once you see his plan, it’s not as crazy as it sounds.
[Alexander] got his inspiration from an earlier Dasung Paperlike Pro teardown that we covered back in 2018. His plan is to shoehorn the e-ink panel into a “headless” Thinkpad T480 laptop. This particular model ES133TT3 display is 13.3 inches (about 40 cm) with a much-better-than-normal laptop resolution of 2200 x 1650 pixels. It is driven over HDMI and is perfect fit for the Thinkpad enclosure.
Unfortunately, these displays haven’t gone down in price since 2018. They’re still in the $1000+ price range, more expensive than many laptops. But if you really want the reduced eye-strain of e-ink in a laptop format, you’re going to have to shell out for it.
It’s a pretty ambitious project. We’re looking forward to following his progress and see how the finished laptop goes together. Do check out the extensive list of e-ink references on his project page, too. If you want to experiment with a less expensive e-ink project, have a look at the PaperTTY project for your Raspberry Pi.