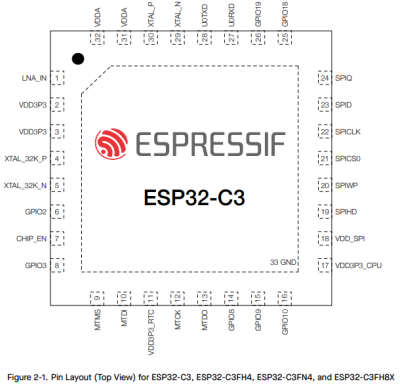
 In an update video by [Hacker University] to an earlier video on ESP32-C3 Super Mini development boards that feature a Flash-less version of this MCU, the question of adding your own Flash IC to these boards is addressed. The short version is that while it is possible, it’s definitely not going to be easy, as pins including SPIHD (19) and SPICLK (22) and SPIQ (24) are not broken out on the board and thus require one to directly solder wires to the QFN pads.
In an update video by [Hacker University] to an earlier video on ESP32-C3 Super Mini development boards that feature a Flash-less version of this MCU, the question of adding your own Flash IC to these boards is addressed. The short version is that while it is possible, it’s definitely not going to be easy, as pins including SPIHD (19) and SPICLK (22) and SPIQ (24) are not broken out on the board and thus require one to directly solder wires to the QFN pads.
Considering how sketchy it would be to have multiple wires running off to an external Flash IC, this raises many questions about the feasibility, as well as cost-effectiveness. Some in the comments to the video remark that instead you may as well swap the MCU with a version that does contain built-in Flash, but this is countered with the argument that a new ESP32-C3 Super Mini board with the right MCU costs as much as a loose MCU from your favorite purveyor of ICs.
Ultimately this lends some credence to calling these zero Flash Super Mini boards a ‘scam’, as their use cases would seem to be extremely limited and their Flash-less nature very poorly advertised.
Continue reading “What To Do With A Flash-less ESP32-C3 Super Mini Board?”



















