OpenSSH has minted their 9.0 release, and it includes a pair of security changes. Unlike most of the releases we cover here, this one has security hardening to prevent issues, not emergency fixes for current ones. First up, the venerable scp/rcp protocol has been removed. Your scp commands will now use SFTP under the hood. The more interesting security change is the new default key exchange, the NTRU algorithm. NTRU is thought to be quantum-hard.
Continue reading “This Week In Security: OpenSSH, Git, And Sort-of NGINX 0-day”
Security Hacks1542 Articles
Just In Case You Want To Charge Your Neighbor’s Tesla
Tesla vehicles have a charging port that is under a cover that only opens on command from a charging station. Well, maybe not only. [IfNotPike] reports that he was able to replay the 315MHz signal using a software defined radio and pop the port open on any Tesla he happened to be near.
Apparently, opening the charging port isn’t the end of the world since there isn’t much you can do with the charging port other than charging the car. At least, that we know of. If history shows anything, it is that anything you can get to will be exploited eventually.
Continue reading “Just In Case You Want To Charge Your Neighbor’s Tesla”
This Week In Security: Vulnerable Boxes, Government Responses, And New Tools
The Cyclops Blink botnet is thought to be the work of an Advanced Persistent Threat (APT) from Russia, and seems to be limited to Watchguard and Asus devices. The normal three and four letter agencies publicized their findings back in February, and urged everyone with potentially vulnerable devices to go through the steps to verify and disinfect them if needed. About a month later, in March, over half the botnet was still online and functioning, so law enforcement took a drastic step to disrupt the network. After reverse-engineering the malware itself, and getting a judge to sign off on the plan, the FBI remotely broke in to 13 of the Watchguard devices that were working as Command and Control nodes. They disinfected those nodes and closed the vulnerable ports, effectively knocking a very large chunk of the botnet offline.
The vulnerability in WatchGuard devices that facilitated the Botnet was CVE-2022-23176, a problem where an “exposed management access” allowed unprivileged users administrative access to the system. That vague description sounds like either a debugging interface that was accidentally included in production, or a flaw in the permission logic. Regardless, the problem was fixed in a May 2021 update, but not fully disclosed. Attackers apparently reversed engineered the fix, and used it to infect and form the botnet. The FBI informed WatchGuard in November 2021 that about 1% of their devices had been compromised. It took until February to publish remediation steps and get a CVE for the flaw.
This is definitely non-ideal behavior. More details and a CVE should have accompanied the fix back in May. As we’ve observed before, obscurity doesn’t actually prevent sophisticated actors from figuring out vulnerabilities, but it does make it harder for users and security professionals to do their jobs. Continue reading “This Week In Security: Vulnerable Boxes, Government Responses, And New Tools”
Build A TPM Module For Your Server
One of the big stories surrounding the announcement of Windows 11 was that it would require support for TPM 2.0, or Trusted Platform Module, to run. This takes the form of an on-board cryptographic processor, which Microsoft claims will help against malware, but which perhaps more importantly for Redmond, can be used to enforce DRM. Part of the standard involves a hardware module, and [Zane] has built a couple of them for ASrock server motherboards.
The chip in question is the Infineon SLB9965, which with a bit of research was found to map more or less directly to the pins of the TPM socket on the motherboard. The interesting thing here lies in the background research it gives into TPMs, and furthermore the links to other resources dealing with the topic. The chances are that most readers needing a TPM will simply buy one, but all knowledge is useful when it comes to these things.
Our weekly security roundup has been keeping an eye on the use of TPMs for a while, and has even shown us some ways that people have used to bypass the modules.
This Week In Security: More State-Sponsored Activity, Spring4Shell
[Editor’s note: There is a second, fake iteration of this column out today. This is obviously the real column.]
An alert from CISA, combined with an unsealed pair of indictments, sheds some new light on how Russian hackers pursue high-value targets. The key malware here is Triton, essentially a rootkit designed for the Tricon safety systems, widely deployed at refineries and other infrastructure facilities. One of the early deployments of this was to a Saudi oil plant in 2017. This deployment seems to have been botched, as it caused malfunctions and shut the plant down for about a week.
The new information is confirmation that the same operators, out of the “Central Scientific Research Institute of Chemistry and Mechanics”, attempted to target US facilities with the same campaign. The Wired coverage initially struck me as odd, as it detailed how these Russian attackers researched US refineries, looking for the most promising targets. How exactly did US intelligence agencies know about the research habits of agents in Russia? The details of the indictment has the answer: They were researching US refineries by downloading papers from the US Department of Energy. As the IP addresses of this Russian research group is known and tracked, it was easy enough for US agencies to make the connection.
Continue reading “This Week In Security: More State-Sponsored Activity, Spring4Shell”
This WeeΚ In Security: Hackerman, Twitter’s Best, And Signs To Watch Out For
[Editor’s note: There is a second, fake iteration of this column out today. This is obviously the real column.]
First off, there’s an amazing video tutorial from [Hackerman], embedded below the break. It’s a beginners guide to temporal displacement through GPU accelerated, cellular-connected partition board. The central flaw that makes this possible is a segmentation violation, accessible through a mode 6 cursor address reset. Watch out, though, because many mainframes actually have a core terminal capable of shutting such an attempt out of the grid altogether.
It’s a great guide, and definitely worth a watch if temporal security tickles your fancy. Watch out, though, because everyday objects can apparently act as bridges, infecting even users with temporal effects.
Continue reading “This WeeΚ In Security: Hackerman, Twitter’s Best, And Signs To Watch Out For”
This Week In Security: Browser In The Browser, Mass Typo-squatting, And /dev/random Upgrades
For every very clever security protocol that keeps people safe, there’s a stupid hack that defeats it in an unexpected way. Take OAuth for instance. It’s the technology that sites are using when they offer to “log in with Facebook”. It’s a great protocol, because it lets you prove your identity using a trusted third party. You don’t have to use a password at whatever site you’re trying to use, you just to be logged in to your Google/Facebook/Apple account, and click the button to allow access. If you’re not logged in, the pop-up window prompts for your username and password, which of course is one way phishing attacks try to steal passwords. So we tell people to look at the URL, and make sure they are actually signing in to the proper site.
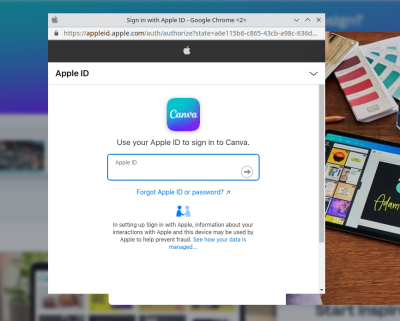
The stupid hack that isn’t stupid, because it works: Recreating the browser window in HTML/CSS. Yep, it’s pretty straightforward to add a div to your site, and decorate it to look just like a browser window, just like an OAuth pop-up. In the appropriate place goes an iframe pointing to the actual phishing form. It looks convincing, but once you’re aware of the game, there’s a dead giveaway — try to move the OAuth window outside the browser window that spawned it. Websites can’t draw outside the browser window or over its window decorations, so this limitation makes it easy to confirm whether this hack is in play. The other saving grace is that a password manager isn’t fooled by this trick at all.
Via: Ars Technica
Typo-squatting At Scale
There’s a typo-squatting campaign going on at NPM, primarily targeted at Azure users. NPM has a packaging feature called “scoped packages”. A scope starts with the at sign, and indicates packages intentionally grouped together. In this case the scope is @azure, including packages like @azure/core-tracing, with over 1.5 million weekly downloads. The typo? Just drop the scope. NPM considers it completely acceptable to have both the @azure/core-tracing and core-tracing packages — in fact, it’s a feature of the scoping system. But forget to include the scope, and you may get a malicious package instead. Over 200 packages were targeted in this way, but have since been pulled by NPM.
The payload was strictly reconnaissance, grabbing directory listings, IP addresses, and the like. It’s likely that the information would be used to craft more malicious future updates, though no such behavior has been observed. This is likely due to how rapidly these packages were caught and removed — after only about two days. The domain used for data collection is 425a2.rt11.ml, so that string showing up in a DNS log somewhere is an indicator that one of these packages were installed.
Lapsus$ Strikes Again, Again
The loose collection of hackers knows as Lapsus$ have potentially scored breaches at both Microsoft and Okta. KrebsonSecurity has a bit more information about the group and the Microsoft case. The group seems to be doing some of their coordination over a Telegram channel, which is open for anyone to join. The group boasted of their exploits on this channel, and Microsoft respondents found and cut their access during the data exfiltration. A 10 GB file has been released containing partial source to Bing search, Bing Maps, and Cortana.
The Okta situation is even murkier, as the released screenshots indicate access back in late January. The access seems to have been limited to a administrative portal, via a Support Engineer’s account. Okta has gone out of their way to assure everyone that there was no actual breach, and the rogue access was quickly dealt with. This seems to be a bit disingenuous, as Lapsus$ was after companies making use of Okta services, and didn’t need to compromise their systems any further. Okta provides access management for other companies, like Cloudflare. There’s likely been some quiet infiltration happening in the months since this happened.
Linux Gets More Random
[Jason Donenfeld], kernel hacker and main developer of Wireguard, has worked recently on the Linux random number generator. A few changes landed in release 5.17, and more are coming in 5.18. He was kind enough to write up some of the interesting changes for our education. He considers his most important contribution to be documentation. I can confirm, among the most frustrating problems a programmer can face is when the documentation has bit-rotted to uselessness.
One of the biggest user-facing changes was the attempt to unify /dev/random and /dev/urandom. We say attempt, because this change caused multiple failures to boot on the kernel’s test setup. Apparently some architectures, specifically when being virtualized, have no method of generating high quality randomness during boot. There next killer feature is the new add_vmfork_randomness() call, that allows a newly cloned virtual machine to request a regeneration of its randomness pool. Without a call like this, the first few random numbers generated by the kernel after a VM fork would be identical — obviously a problem.
Internally, the randomness code retires the venerable SHA-1 algorithm, replacing it with the more modern BLAKE2 hash function. An interesting advantage is that BLAKE2 is intentionally a very fast algorithm, so the kernel gains a bit of performance when generating random numbers. The rest of the changes delve into more complicated cryptography considerations. Definitely worth reading if you’re interested.
Western Digital NAS RCE
We’ve covered plenty of vulnerabilties and attacks in NAS boxes from QNAP and Synology, but this week it’s Western Digital getting in on the action. Thankfully it’s research from NCC Group, demonstrated at Pwn2Own 2021, and fixed in a January update. This Remote Code Execution (RCE) vulnerability is in how the NAS handles the Apple Filing Protocol (AFP), and was actually a problem in the Netatalk project. AFP supports storing file metadata as a separate file, for the sake of compatibility. These files are in the AppleDouble format, are take the name of their parent file, prepended with a ._. The kicker is that these files can also be accessed using the Windows SMB protocol, allowing direct manipulation of the metadata file. The function that parses the metadata file does indeed detect a malformed data structure, and logs an error to that effect, but fails to fail — it goes ahead and processes the bad data.
This continue-on-error is the central flaw, but actually building an exploit required a data leak to defeat the address layout randomization in place on the device. A simpler first step was to write memory locations into the AppleDouble file, and use SMB access to read it. With the leaked address in hand, the full exploit was easy. This would be bad enough, but these devices ship with a “Public” share world-accessible over SMB and AFP. This configuration makes it a pre-auth RCE. And this demonstrates the purpose of Pwn2Own — it was discovered, made the researchers a bit of money, and was fixed before the details were made public.