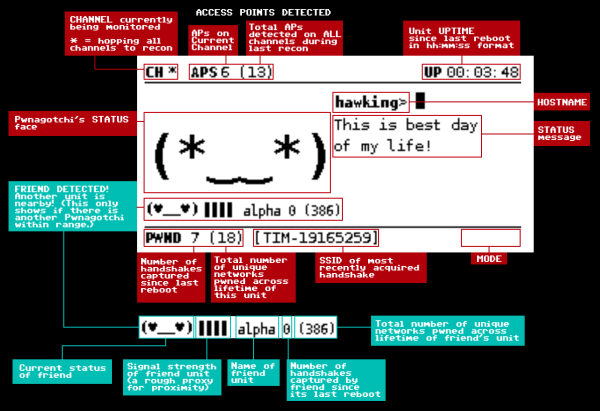
A government is going after a human rights activists in Morocco. It sounds familiar, but I don’t think Humphrey Bogart is running the gin joint this time around.
Questionable Casablanca references aside, Amnesty International has reported another attack against human rights workers. In this case, a pair of Moroccan activists were targeted with what appears to be NSO’s Pegasus malware suite. Researchers identified text message phishing that led to malicious web pages, as well as HTTP man in the middle attacks against their mobile devices. Once the target was successfully directed to the malicious site, A collection of zero-day vulnerabilities were used to compromise the phone with the NSO malware.
NSO is an Israeli company that specializes in building malware and other cybersecurity tools for governments. As you can imagine, this specialization has earned NSO the scorn of quite a few organizations. NSO claims to have a policy framework in place that allows them to evaluate and terminate the use of their software when it is deemed illegal or abusive, but due to the nature of their contracts, that process is anything but transparent. Continue reading “This Week In Security: A Digital Café Américain, The Linux Bugs That Weren’t, The Great Nation, And More”










 The USB Armory Mk II is powered by an upgraded 900 MHz ARM Cortex-A7 processor, though it retains the same 512 MB of RAM from the previous version. Like the original, there’s a micro SD slot to hold the Linux operating system, but this time it’s supplemented with an onboard 16 GB eMMC chip. There’s even a physical switch that allows the user to choose which storage device they want to boot from. Other additions for the Mk II include Bluetooth connectivity, and a hardware true random number generator (TRNG).
The USB Armory Mk II is powered by an upgraded 900 MHz ARM Cortex-A7 processor, though it retains the same 512 MB of RAM from the previous version. Like the original, there’s a micro SD slot to hold the Linux operating system, but this time it’s supplemented with an onboard 16 GB eMMC chip. There’s even a physical switch that allows the user to choose which storage device they want to boot from. Other additions for the Mk II include Bluetooth connectivity, and a hardware true random number generator (TRNG).








