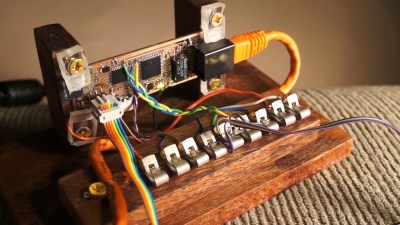
Trent Fehl is an engineer who has worked for such illustrious outfits as SpaceX and Waymo. When he got into baking, he brought those engineering skills home to solve a classic problem in the kitchen: keeping a sourdough starter within the ideal, somewhat oppressive range of acceptable temperatures needed for successful fermentation.
A sourdough starter is a wad of wild yeasts that you make yourself using flour, water, and patience. It’s good for a lot more than just sourdough bread — you can scoop some out of the jar and use it to make pancakes, waffles, pretzels, and a host of other bread-y delights. A starter is a living thing, a container full of fermentation that eats flour and has specific temperature needs. Opinions differ a bit, but the acceptable temperature range for active growth is about 60 F to 82 F. Too cold, and the starter will go dormant, though it can be revived with a little love. But if the starter gets too hot, all the yeasts and bacteria will die.
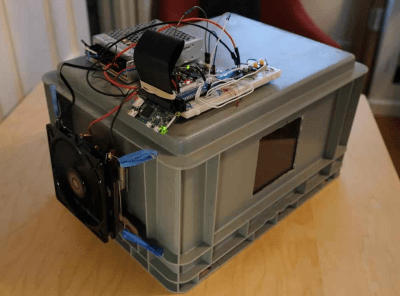 While there are of course commercial products out there that attempt to solve this problem of temperature control, most of them seem to be aimed at people who live in some wonderland that never gets warmer than 80F. Most of these devices can’t cool, they only provide heat. But what if you live in a place with seasons where the climate ranges from hot and humid to cold and dry?
While there are of course commercial products out there that attempt to solve this problem of temperature control, most of them seem to be aimed at people who live in some wonderland that never gets warmer than 80F. Most of these devices can’t cool, they only provide heat. But what if you live in a place with seasons where the climate ranges from hot and humid to cold and dry?
The answer lies within Chamber, a temperature-regulated haven Trent created that lets these wild yeasts grow and thrive. It uses a Peltier unit to heat and cool the box as needed to keep the mixture fermenting at 26°C /78.8°F.
Thanks to the Peltier unit, Trent can change the temperature inside the chamber simply by alternating the direction of current flow through the Peltier. He’s doing this with an H-bridge module driven by a Raspberry Pi Zero. When it starts to get too warm in the chamber, the fan on the outside wall vents the heat away. A second fan inside the chamber pulls warm air in when it gets too cold.
Trent says that Chamber performs really well, and he’s recorded temperatures as low as 60F and as high as 82F. He mostly uses it for sourdough, but it could work for other temperature-sensitive food sciences like pickling, growing mushrooms, or making yogurt. We think it could be ideal for fermenting kombucha, too.
Chamber works well enough that Trent has put further development on the back burner while he makes use of it. He does have several ideas for improvements, so if you want to help, check out his website and Github repo.
Continue reading “Engineering Your Way To Better Sourdough (and Other Fermented Goods)” →