It looks like the ongoing semiconductor shortage isn’t getting any better, and if the recent spate of computer thefts from semi trucks is any indication, it’s only going to get worse. Thieves seem to be targeting the Freightliner Cascadia, probably the most popular heavy freight truck on the road in North America today, with “smash and grab” thefts targeting the CPC4, or Common Powertrain Control module. These modules are sitting ducks — they’re easy to locate and remove, the chip shortage has made legit modules nearly unobtanium from dealers, and the truck won’t run without them. That’s driven the black market price for a CPC up to $8,000 or more, making them a tempting target. And it’s not only individual trucks parked in truck stop lots that are being hit; gangs are breaking into trucking company lots and bricking dozens of trucks in short order. So the supply chain problem which started the semiconductor shortage caused the module shortage, which drives the thieves to steal modules and take trucks off the road, which only worsens the supply chain shortage that started the whole thing. Nice positive feedback loop.
crime17 Articles
Hackaday Links: July 18, 2021
Tell the world that something is in short supply, and you can bet that people will start reacting to that news in the ways that make the most sense to them — remember the toilet paper shortage? It’s the same with the ongoing semiconductor pinch, except that since the item in short supply is (arguably) more valuable than toilet paper, the behavior and the risks people are willing to take around it are even more extreme. Sure, we’ve seen chip hoarding, and a marked rise in counterfeit chips. But we’d imagine that this is the first time we’ve seen chip smuggling quite like this. The smuggler was caught at the Hong Kong-Macao border with 256 Core i7 and i9 processors, valued at about $123,000, strapped to his legs and chest. It reminds us more of “Midnight Express”-style heroin smuggling, although we have to say we love the fact that this guy chose a power of 2 when strapping these babies on.
Speaking of big money, let’s say you’ve pulled off a few chip heists without getting caught, and have retired from the smuggling business. What is one to do with the ill-gotten gains? Apparently, there’s a big boom in artifacts from the early days of console gaming, so you might want to start spreading some money around there. But you’d better prepare to smuggle a lot of chips: last week, an unopened Legend of Zelda cartridge for the NES sold for $870,000 at auction. Not to be outdone, two days later someone actually paid $1.56 million for a Super Mario 64 cartridge, this time apparently still in the tamperproof container that displayed it on a shelf somewhere in 1996. Nostalgia can be an expensive drug.
And it’s not just video games that are commanding high prices these days. If you’ve got a spare quarter million or so, why not bid on this real Apollo Guidance Computer and DSKY? The AGC is a non-flown machine that was installed in LTA-8, the “lunar test article” version of the Landing Module (LM) that was used for vacuum testing. If the photos in the auction listing seem familiar, it’s with good reason: this is the same AGC that was restored to operating condition by Carl Claunch, Mike Stewart, Ken Shiriff, and Marc Verdiell. Sotheby’s estimates the value at $200,000 to $300,000; in a world of billionaire megalomaniacs with dreams of space empires, we wouldn’t be surprised if a working AGC went for much, much more than that.
Meanwhile, current day space exploration is going swimmingly. Just this week NASA got the Hubble Space Telescope back online, which is great news for astronomers. And on Mars, the Ingenuity helicopter just keeps on delivering during its “operations demonstration” mission. Originally just supposed to be a technology demonstration, Ingenuity has proven to be a useful companion to the Perseverance rover, scouting out locations of interest to explore or areas of hazard to avoid. On the helicopter’s recent ninth flight, it scouted a dune field for the team, providing photographs that showed the area would be too dangerous for the rover to cross. The rover’s on-board navigation system isn’t great at seeing sand dunes, so Ingenuity’s images are a real boon to mission planners, not to mention geologists and astrobiologists, who are seeing promising areas of the ancient lakebed to explore.
And finally, most of us know all too well how audio feedback works, and all the occasions to avoid it. But what about video feedback? What happens when you point a camera that a screen displaying the image from the camera? Fractals are what happens, or at least something that looks a lot like fractals. Code Parade has been playing with what he calls “analog fractals”, which are generated just by video feedback and not by computational means. While he’d prefer to do this old school with analog video equipment, it easy enough to replicate on a computer; he even has a web page that lets you arrange a series of virtual monitors on your screen. Point a webcam at the screen, and you’re off on a fractal journey that constantly changes and shifts. Give it a try.
Russian Doomsday Radios Go Missing
Normally we like hearing about old military gear going on the surplus market. But if you encounter some late-model Russian radio and crypto equipment for sale you might want to make sure it isn’t hot (English translation). If you prefer not picking through the machine translation to English, the BBC also has a good write-up.
The Russians maintain four large planes set up as flying command and control bunkers in case of nuclear war — so-called “doomsday planes.” Like the U.S. ABNBC (better known as Looking Glass) fleet, the planes can provide the President or other senior leaders a complete command capability while in flight. As you might expect, the radios and gear on the plane are highly classified.
Spoof A Skimmer For Peace Of Mind
It’s a sad commentary on the state of the world when it becomes a good practice to closely inspect the card reader on every ATM and gas pump for the presence of a skimmer. The trouble is, even physically yanking on the reader may not be enough, as more sophisticated skimmers now reside safely inside the device, sipping on the serial comms output of the reader and caching it for later pickup via Bluetooth. Devilishly clever stuff.
Luckily, there’s an app to detect these devices, and the prudent consumer might take solace when a quick scan of the area reveals no skimmers in operation. But is that enough? After all, how do you know the smartphone app is working? This skimmer scammer scanner — or is that a skimmer scanner scammer? — should help you prove you’re being as safe as possible.
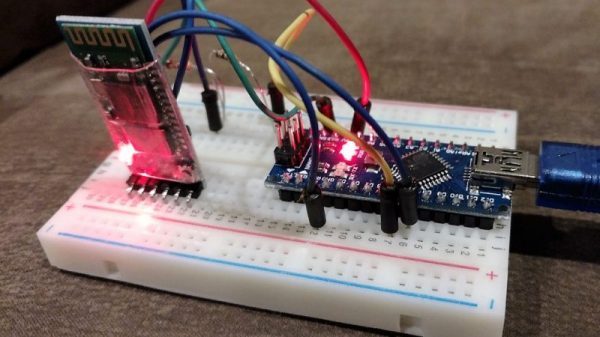
The basic problem that [Ben Kolin] is trying to solve here is: how do you prove a negative? In other words, one could easily write an app with a hard-coded “This Area Certified Zebra-Free” message and market it as a “Zebra Detector,” and 99.999% of the time, it’ll give you the right results. [Ben]’s build provides the zebra, as it were, by posing as an active skimmer to convince the scanner app that a malicious Bluetooth site is nearby. It’s a quick and dirty build with a Nano and a Bluetooth module and a half-dozen lines of code. But it does the trick.
Need a primer on the nefarious world of skimming? Here’s an overview of how easy skimming has become, and a teardown of a skimmer captured in the wild.
Flush Out Car Thieves With A Key Fob Jammer Locator
We all do it — park our cars, thumb the lock button on the key fob, and trust that our ride will be there when we get back. But there could be evildoers lurking in that parking lot, preventing you from locking up by using a powerful RF jammer. If you want to be sure your car is safe, you might want to scan the lot with a Raspberry Pi and SDR jammer range finder.
Inspired by a recent post featuring a simple jammer detector, [mikeh69] decide to build something that would provide more directional information. His jammer locator consists of an SDR dongle and a Raspberry Pi. The SDR is set to listen to the band used by key fobs for the continuous, strong emissions you’d expect from a jammer, and the Pi generates a tone that varies relative to signal strength. In theory you could walk through a parking lot until you get the strongest signal and locate the bad guys. We can’t say we’d recommend confronting anyone based on this information, but at least you’d know your car is at risk.
We’d venture a guess that a directional antenna would make the search much easier than the whip shown. In that case, brushing up on Yagi-Uda antenna basics might be a good idea.
Autonomous Delivery: Your Impulse Buys Will Still Be Safe
I heard a “Year in Review” program the other day on NPR with a BBC World Service panel discussion of what’s ahead for 2017. One prediction was that UAV delivery of packages would be commonplace this year, and as proof the commentator reported that Amazon had already had a successful test in the UK. But he expressed skepticism that it would ever be possible in the USA, where he said that “the first drone that goes over somebody’s property will be shot down and the goods will be taken.”
He seemed quite sincere about his comment, but we’ll give him the benefit of the doubt that he was only joking to make a point, not actually grotesquely ignorant about the limitations of firearms or being snarky about gun owners in the US. Either way, he brings up a good point: when autonomous parcel delivery is commonplace, who will make sure goods get to the intended recipient?
Continue reading “Autonomous Delivery: Your Impulse Buys Will Still Be Safe”
Remote Access Programs Are Good Security For Laptops

Don’t be [Gabriel Meija], the criminal pictured above. He stole [Jose Caceres]’ laptop, but didn’t realize that [Caceres] had installed a remote access program to track the activity on the laptop. Although the first few days were frustrating, as [Meija] didn’t seem to be using the laptop for anything but porn, [Caceres]’ luck turned when he noticed that an address was being typed in. [Caceres] turned the information over to police, who were able to find [Meija] and charge him with fourth-degree grand larceny. It’s not the first time that tech-savvy consumers have relied on remote access programs to capture the criminals who’ve stolen their computer equipment, and it certainly won’t be the last, as the technology becomes more readily available to consumers.