Looking to get into fault injection for your reverse engineering projects, but don’t have the cash to lay out for the necessary hardware? Fear not, for the tools to glitch a chip may be as close as the nearest barbecue grill.
If you don’t know what chip glitching is, perhaps a primer is in order. Glitching, more formally known as electromagnetic fault injection (EMFI), or simply fault injection, is a technique that uses a pulse of electromagnetic energy to induce a fault in a running microcontroller or microprocessor. If the pulse occurs at just the right time, it may force the processor to skip an instruction, leaving the system in a potentially exploitable state.
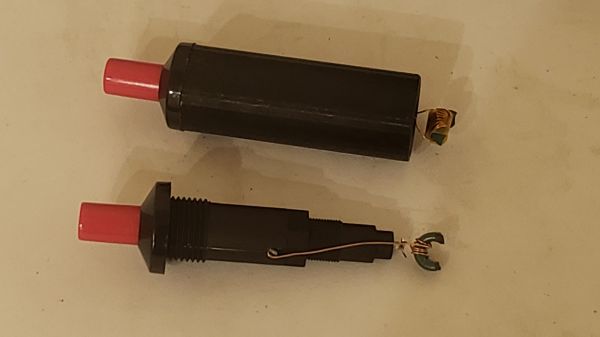
EMFI tools are commercially available — we even recently featured a kit to build your own — but [rqu]’s homebrew version is decidedly simpler and cheaper than just about anything else. It consists of a piezoelectric gas grill igniter, a little bit of enameled magnet wire, and half of a small toroidal ferrite core. The core fragment gets a few turns of wire, which then gets soldered to the terminals on the igniter. Pressing the button generates a high-voltage pulse, which gets turned into an electromagnetic pulse by the coil. There’s a video of the tool in use in the Twitter thread, showing it easily glitching a PIC running a simple loop program.
To be sure, a tool as simple as this won’t do the trick in every situation, but it’s a cheap way to start exploring the potential of fault injection.
Thanks to [Jonas] for the tip.