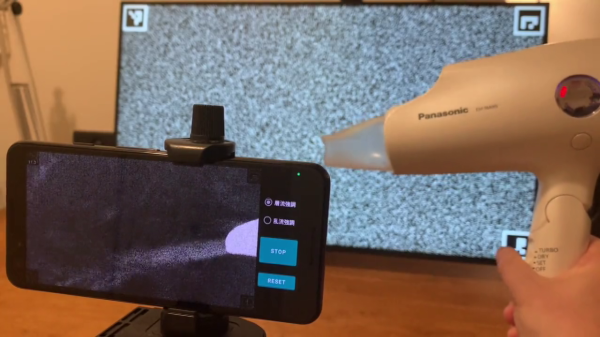
Multiple people have recently shared this exciting demonstration (nitter) with us – visualizing airflow using a smartphone, called ‘background-oriented schlieren’. On a hot summer day, you might see waves in the air – caused by air changing density as it warms up, and therefore refracting the light differently. Schlieren photography is an general set of techniques for visualizing fluid flow, but of course, it can also be applied to airflow. In this case, using some clever optical recognition tricks, this schlieren method lets you visualize flow of air using only your Android smartphone’s high resolution camera and a known-pattern printed background! Continue reading “Observe Airflow Using Smartphone And Background-Oriented Schlieren”
phone124 Articles
The Case For Designer Landline Phones
Long before the idea of hot dog-shaped iPhone cases, Otter Boxen, or even those swappable Nokia face plates, people were just as likely to express themselves with their landline phones. Growing up at my house in the 80s, the Slimline on the kitchen wall was hidden inside a magneto wall set from the early 1900s, the front of which swung out to reveal the modern equipment behind it. Back in my bedroom, I had the coolest phone ever, a see-through Unisonic with candy-colored guts. Down in the basement was my favorite extension, tactility-wise: a candy apple-red wall unit with dimly-lit circular push buttons that were springy and spongy and oh-so fun to dial.
Popular culture shows us that people were dreaming of cool telephone enclosures before they were even a thing. Obviously, TV secret agent Maxwell Smart’s shoe phone wasn’t plausible for the technology of that era, but it also wasn’t really feasible for aesthetic reasons. For decades, phone subscribers had to use whatever equipment Ma Bell had to offer, and you couldn’t just buy the things outright at the mall — you had to lease the hardware from her, and pay for the service.
A Home Payphone
We can’t condone what [Bertrand] did as a kid to make him a fan of payphones, but we get his desire to have one of his own in his home. Even if you don’t want one yourself, he’s got some good shots of the insides of a real phone that came from a casino in Vegas.
As you might expect, these phones were built like tanks. They obviously took a lot of abuse. We had to wonder how much each one cost to produce back in the day. Cleaning up an old phone and getting it to work doesn’t seem like a big effort, but there’s one thing we didn’t think about. Turns out there is a backplate that holds the 50-pound phone up and you need special studs that screw into the phone to hold it up while you put screws through both pieces.
He did connect the phone successfully to a regular phone jack, but his goal was to let his 5-year-old use the phone so he decided to actually wire it to a phone line simulator that just provides a connection between two phones.
New York City recently ripped out its last payphones. They were replaced with multipurpose kiosks, but there are still privately-owned payphones in the city. Of course, you can always use an old payphone as a platform for a different project.
Build A Prop For A TV Premiere? Stranger Things Have Happened
Some guys get all the breaks. [Guy Dupont] had the honor of building a working, interactive wall-mount landline phone for the red carpet premiere of a certain TV show. The phone was to be an Easter egg inside an 80s-style pizzeria set. About every two minutes the phone would ring, and anyone brave enough to answer would be greeted with either a fake pizza order, an old answering machine message, or a clip from The Show That Cannot Be Mentioned.
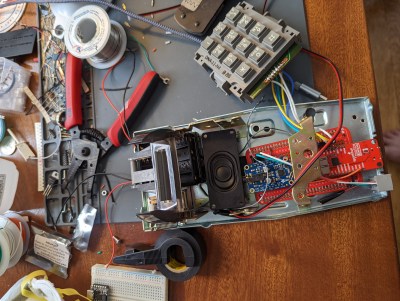
So the phone doesn’t work-work, but the nostalgia is strong — picking up the receiver when the phone isn’t ringing results in a dial tone, and button pushing leads to the busy signal. Those old pleasant-but-stern operator recordings would have been cool, but there was only so much time. (Your call cannot be completed as dialed. Please check the number and try again.)
[Guy] used a SparkFun RP2040 to handle input from the DTMF keypad and play the tones, the dial and busy signals, and the various recordings into the ear of the receiver.
Instead of messing around with the high voltage needed to drive the original ringer and bell, [Guy] used a small speaker to play the ringing sound. Everything runs on eight AAs tucked under the keypad, which is stepped down to 5 V.
This project was built under fairly dramatic duress, which makes it that much more exciting to watch the build video after the break. With just five days to get the phone working and in the mail, [Guy] holed up on the floor of his office, his messy mid-move refuge from a house plagued by COVID. Unfortunately, the whole pizzeria thing fell through, so [Guy]’s phone will not get to have its moment on the red carpet. But at least it’s on the site that’s black and white and read all over.
[Guy] is no stranger to the old tech/new spec game. Remember that time he shoehorned Spotify into an iPod Classic?
Continue reading “Build A Prop For A TV Premiere? Stranger Things Have Happened”
Replaceable Batteries Are Coming Back To Phones If The EU Gets Its Way
Back in the day, just about everything that used a battery had a hatch or a hutch that you could open to pull it out and replace it if need be. Whether it was a radio, a cordless phone, or a cellphone, it was a cinch to swap out a battery.
These days, many devices hide their batteries, deep beneath tamper-proof stickers and warnings that state there are “no user serviceable components inside.” The EU wants to change all that, though, and has voted to mandate that everything from cellphones to e-bikes must have easily replaceable batteries, with the legislation coming into effect as soon as 2024.
Continue reading “Replaceable Batteries Are Coming Back To Phones If The EU Gets Its Way”
Here’s How Those Battery-Free Flashing Phone Stickers Worked
The late 90s and early 2000s were a breakout time for mobile phones, with cheap GSM handsets ushering in the era in which pretty much everybody had a phone. Back then, a popular way to customize one’s phone was to install a sticker that would flash when the phone rang. These required no batteries or any other connection to the phone, and [Big Clive] has dived in to explain how they worked.
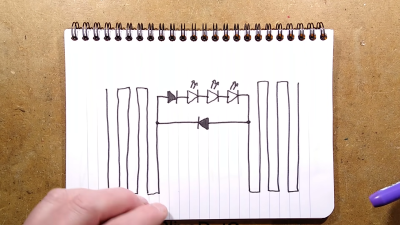
It’s an old-fashioned teardown that requires a bit of cutting to get inside the sticker itself. A typical example had three LEDs in series for a total voltage drop of around 7V, hooked up to two diodes and a PCB trace antenna. A later evolution used raw unpackaged components bonded to the PCB. Future versions went down to a single diode, using the LEDs to serve as the second. The basic theory was that the PCB traces would pick up RF transmitted by the phone when a call was coming in, lighting the LEDs.
In the 2G era, the freuqencies used were on the order of 300 MHz to 1.9GHz. A combination of the change in frequencies used by modern phone technology and the lower transmit powers used by handsets means that the stickers don’t work properly with modern phones according to [Big Clive].
Incidentally, you might like to consider running your own old-school cellphone network. Video after the break.
Continue reading “Here’s How Those Battery-Free Flashing Phone Stickers Worked”
A Rotary Phone As A Computer Peripheral
It’s an age-old conundrum for anyone working with retro hardware: preserve its original condition or not? The answer depends so often on a complex mix of how rare, obsolete or unusable the device is in its original form , and what the intended use for the device will be. For [Typhon Mind] who needed a novelty method of recording best wishes at a wedding through an old dial phone there was no need for it to be entirely original, so the solution was to turn it into a USB device for a host computer.
Out went the original circuitry, and in came a USB hub, a USB audio interface, and an Arduino. The original earpiece would suffice, but the microphone was replaced with a more modern one. The Arduino will register the cradle switch, and also power a set of LED addressable lights under the unit.
The result is a phone that retains all its looks, but has a new life as a PC peripheral. We’d venture to suggest that also using the Arduino to read the dial and produce DTMF tones might make it a valid peripheral for a VOIP application and complete the transformation, but that’s something that could be done at a later date. Maybe it could even be given a GSM makeover.