Finding broken test gear and fixing it up to work again is a time-honored tradition among hackers. If you’re lucky, that eBay buy will end up being DOA because of a popped fuse or a few bad capacitors, and a little work with snips and a soldering iron will earn you a nice piece of test gear and bragging rights to boot.
Some repairs, though, are in a class by themselves, like this memory module transplant for a digital scopemeter. The story began some time ago when [FeedbackLoop] picked up a small lot of broken Fluke 199C scopemeters from eBay. They were listed as “parts only”, which is never a good sign, and indeed the meters were in various states of disassembly and incompleteness.
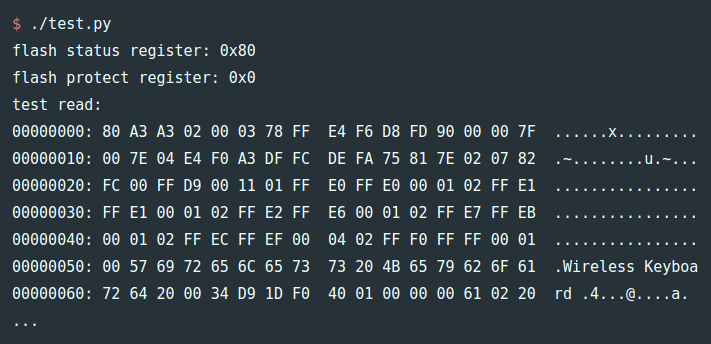
The subject of the video below was missing several important bits, like a battery and a power connector, but most critically, its memory module. Luckily, the other meter had a good module, making reverse engineering possible. That effort started with liberating the two RAM chips and two flash chips, all of which were in BGA packages, from the PCB. From there each chip went into a memory programmer to read its image, which was then written to new chips. The chip-free board was duplicated — a non-trivial task for a six-layer PCB — and new ones ordered. After soldering on the programmed chips and a few passives, the module was plugged in, making the meter as good as new.
While we love them all, it’s clear that there are many camps of test gear collectors. You’ve got your Fluke fans, your H-P aficionados, the deep-pocketed Keithley crowd — but everyone loves Tektronix.
Continue reading “Cloned Memory Module Fixes Broken Scopemeter”