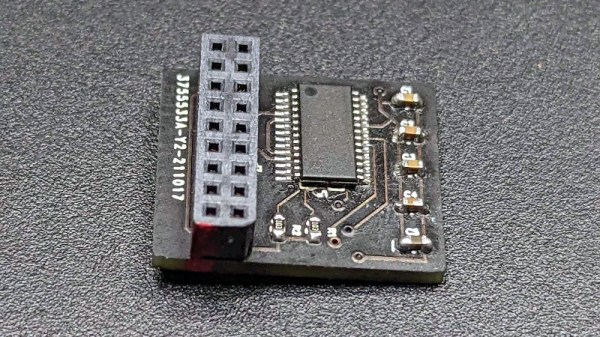
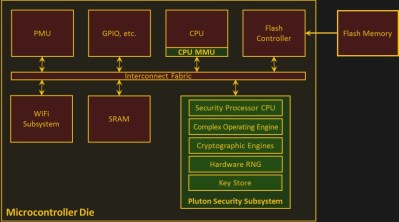
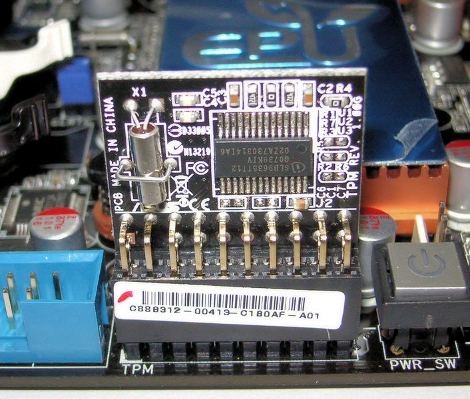
One of the big stories surrounding the announcement of Windows 11 was that it would require support for TPM 2.0, or Trusted Platform Module, to run. This takes the form of an on-board cryptographic processor, which Microsoft claims will help against malware, but which perhaps more importantly for Redmond, can be used to enforce DRM. Part of the standard involves a hardware module, and [Zane] has built a couple of them for ASrock server motherboards.
The chip in question is the Infineon SLB9965, which with a bit of research was found to map more or less directly to the pins of the TPM socket on the motherboard. The interesting thing here lies in the background research it gives into TPMs, and furthermore the links to other resources dealing with the topic. The chances are that most readers needing a TPM will simply buy one, but all knowledge is useful when it comes to these things.
Our weekly security roundup has been keeping an eye on the use of TPMs for a while, and has even shown us some ways that people have used to bypass the modules.