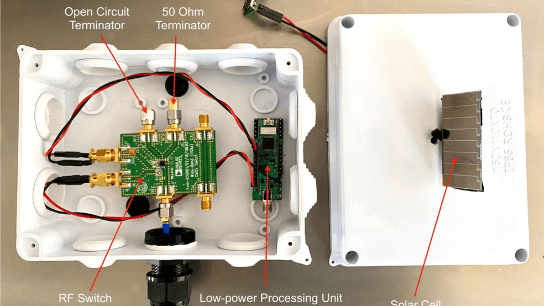
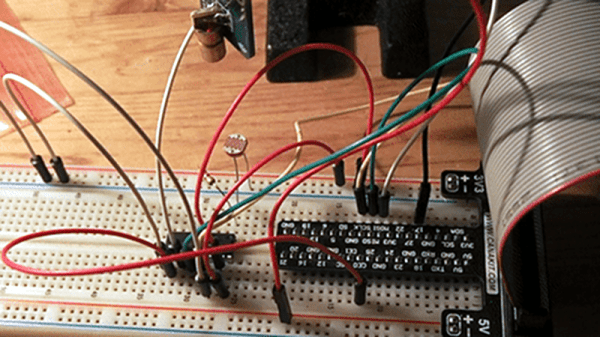
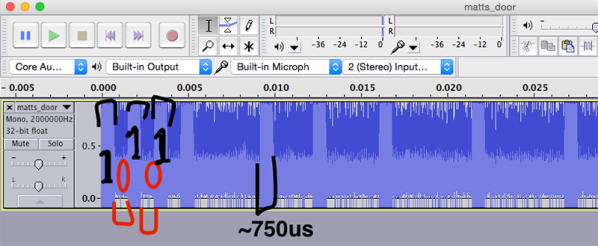
One of the great things about the Hackaday community is how quickly you find out what you don’t know. That’s not a bad thing, of course; after all, everyone is here to get smarter, right? So let’s work together to get our heads around this paper (PDF) by [Zerina Kapetanovic], [Miguel Morales], and [Joshua R. Smith] from the University of Washington, which purports to construct a low-throughput RF transmitter from little more than a resistor.
This witchcraft is made possible thanks to Johnson noise, also known as Johnson-Nyquist noise, which is the white noise generated by charge carriers in a conductor. In effect, the movement of electrons in a material thanks to thermal energy produces noise across the spectrum. Reducing interference from Johnson noise is why telescopes often have their sensors cooled to cryogenic temperatures. Rather than trying to eliminate Johnson noise, these experiments use it to build an RF transmitter, and with easily available and relatively cheap equipment. Continue reading “A Single-Resistor Radio Transmitter, Thanks To The Power Of Noise”