You’re a contractor and people are paying you to work in your pajamas. It’s a life of luxury, but when tax time comes, you are in a world of hurt and you wonder why you even do it. Taxes are tricky, but there are some tools you can use to make it less painful on your pocketbook. With planning and diligence, you can significantly increase the amount of money that stays in your bank account. Continue reading “Life On Contract: Hacking Your Taxes”
Year: 2017
Official Launch Of The Asus Tinker Board
Earlier this year, a new single board computer was announced, and subsequently made its way onto the market. The Tinker Board was a little different from the rest of the crop of Raspberry Pi lookalikes, it didn’t come from a no-name company or a crowdfunding site, instead it came from a trusted name, Asus. As a result, it is a very high quality piece of hardware, upon which we remarked when we reviewed it.
Unfortunately, though we were extremely impressed with the board itself, we panned the Asus software and support offering of the time, because it was so patchy as to be non-existent. We had reached out to Asus while writing the review but received no answer, but subsequently they contacted us with a sorry tale of some Tinker Boards finding their way onto the market early, before their official launch and before they had put together their support offering. We updated our review accordingly, after all it is a very good product and we didn’t like to have to pan it in our review.
This week then, news has come through from Asus that they have now launched the board officially. There is a new OS version based on Debian 9, which features hardware acceleration for both the Chromium web browser and the bundled UHD media player. There is also an upcoming Android release though it is still in beta at time of writing and there is little more information.
The Tinker Board is one of the best of the current crop of Raspberry Pi-like single board computers, and it easily trounces the Pi itself on most counts. To see it launched alongside a meaningful software and support offering will give it a chance to prove itself. In our original review we urged tech-savvy readers to buy one anyway, now it has some of the backup it deserves we’d urge you to buy one for your non-technical family members too.
Neural Networks: You’ve Got It So Easy
Neural networks are all the rage right now with increasing numbers of hackers, students, researchers, and businesses getting involved. The last resurgence was in the 80s and 90s, when there was little or no World Wide Web and few neural network tools. The current resurgence started around 2006. From a hacker’s perspective, what tools and other resources were available back then, what’s available now, and what should we expect for the future? For myself, a GPU on the Raspberry Pi would be nice.
White-hat Botnet Infects, Then Secures IoT Devices
[Symantec] Reports Hajime seems to be a white hat worm that spreads over telnet in order to secure IoT devices instead of actually doing anything malicious.
[Brian Benchoff] wrote a great article about the Hajime Worm just as the story broke when first discovered back in October last year. At the time, it looked like the beginnings of a malicious IoT botnet out to cause some DDoS trouble. In a crazy turn of events, it now seems that the worm is actually securing devices affected by another major IoT botnet, dubbed Mirai, which has been launching DDoS attacks. More recently a new Mirai variant has been launching application-layer attacks since it’s source code was uploaded to a GitHub account and adapted.
Hajime is a much more complex botnet than Mirai as it is controlled through peer-to-peer propagating commands through infected devices, whilst the latter uses hard-coded addresses for the command and control of the botnet. Hajime can also cloak its self better, managing to hide its self from running processes and hide its files from the device.
The author can open a shell script to any infected machine in the network at any time, and the code is modular, so new capabilities can be added on the fly. It is apparent from the code that a fair amount of development time went into designing this worm.
So where is this all going? So far this is beginning to look like a cyber battle of Good vs Evil. Or it’s a turf war between rival cyber-mafias. Only time will tell.
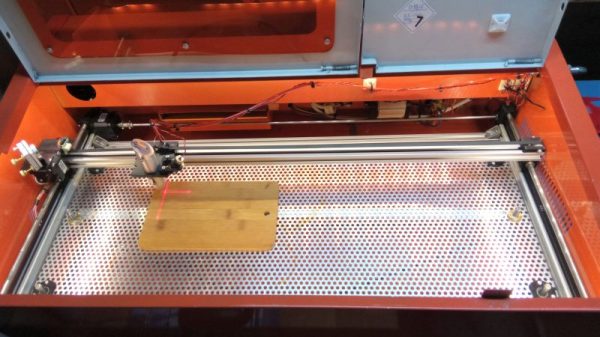
Laser Surgery: Expanding The Bed Of A Cheap Chinese Laser Cutter
Don’t you just hate it when you spend less than $400 on a 40-watt laser cutter and it turns out to have a work area the size of a sheet of copy paper? [Kostas Filosofou] sure did, but rather than stick with that limited work envelope, he modified his cheap K40 laser cutter so it has almost five times the original space.
The K40 doesn’t make any pretenses — it’s a cheap laser cutter and engraver from China. But with new units going for $344 on eBay now, it’s almost a no-brainer. Even with its limitations, you’re still getting a 40-watt CO2 laser and decent motion control hardware to play with. [Kostas] began the embiggening by removing the high-voltage power supply from its original space-hogging home to the right of the work area. With that living in a new outboard enclosure, a new X-Y gantry of extruded aluminum rails and 3D-printed parts was built, and a better exhaust fan was installed. Custom mirror assemblies were turned, better fans were added to the radiator, and oh yeah — he added a Z-axis to the bed too.
We’re sure [Kostas] ran the tab up a little on this build, but when you’re spending so little to start with, it’s easy to get carried away. Speaking of which, if you feel the need for an even bigger cutter, an enormous 100-watt unit might be more your style.
Continue reading “Laser Surgery: Expanding The Bed Of A Cheap Chinese Laser Cutter”
Arbitrary Code Execution Is In Another Castle!
When one buys a computer, it should be expected that the owner can run any code on it that they want. Often this isn’t the case, though, as most modern devices are sold with locked bootloaders or worse. Older technology is a little bit easier to handle, however, but arbitrary code execution on something like an original Nintendo still involves quite a lot of legwork, as [Retro Game Mechanics Explained] shows with the inner workings of Super Mario Brothers 3.
While this hack doesn’t permanently modify the Nintendo itself, it does allow for arbitrary code execution within the game, which is used mostly by speedrunners to get to the end credits scene as fast as possible. To do this, values are written to memory by carefully manipulating on-screen objects. Once the correct values are entered, a glitch in the game involving a pipe is exploited to execute the manipulated memory as an instruction. The instruction planted is most often used to load the Princess’s chamber and complete the game, with the current record hovering around the three-minute mark.
If you feel like you’ve seen something like this before, you are likely thinking of the Super Mario World exploit for the SNES that allows for the same style of arbitrary code execution. The Mario 3 hack, however, is simpler to execute. It’s also worth checking out the video below, because [Retro Game Mechanics Explained] goes into great depth about which values are written to memory, how they are executed as an instruction, and all of the other inner workings of the game that allows for an exploit of this level.
Continue reading “Arbitrary Code Execution Is In Another Castle!”
ESP32’s Dev Framework Reaches 2.0
We’ve been watching the development of the ESP32 chip for the last year, but honestly we’ve been a little bit cautious to throw all of our friendly ESP8266s away just yet. Earlier this month, Espressif released version 2.0 of their IoT Development Framework (ESP-IDF), and if you haven’t been following along, you’ve missed a lot.
We last took a serious look at the IDF when the chips were brand-new, and the framework was still taking its first baby steps. There was no support for such niceties as I2C and such at the time, but you could get both cores up and running and the thing connected to the network. We wanted to test out the power-save modes, but that wasn’t implemented yet either. In short, we were watching the construction of a firmware skyscraper from day one, and only the foundation had been poured.
But what a difference eight months make! Look through the GitHub changes log for the release, and it’s a totally new ballgame. Not only are their drivers for I2C, I2S, SPI, the DAC and ADCs, etc, but there are working examples and documentation for all of the above. Naturally, there are a ton of bugfixes as well, especially in the complex WiFi and Bluetooth Low Energy stacks. There’s still work left to do, naturally, but Espressif seems to think that the framework is now mature enough that they’ve opened up their security bug bounty program on the chip. Time to get hacking!