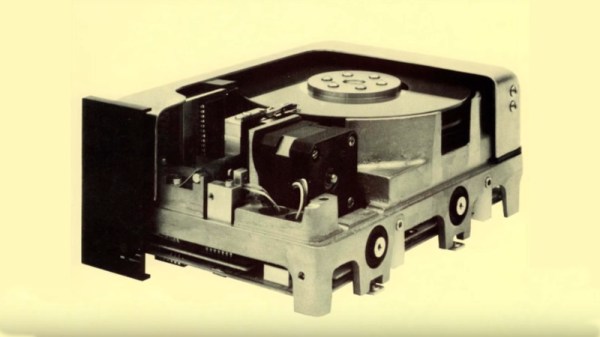
Mass storage has come a long way since the introduction of the personal computer. [Tech Time Traveller] has an interesting video about the dawn of PC hard drives focusing on a company called MiniScribe. After a promising start, they lost an IBM contract and fell on hard times.
Apparently, the company was faking inventory to the tune of $15 million because executives feared for their jobs if profits weren’t forthcoming. Once they discovered the incorrect inventory, they not only set out to alter the company’s records to match it, but they also broke into an outside auditing firm’s records to change things there, too.
Senior management hatched a plan to charge off the fake inventory in small amounts to escape the notice of investors and government regulators. But to do that, they need to be able to explain where the balance of the nonexistent inventory was. So they leased a warehouse to hold the fraud inventory and filled it with bricks. Real bricks like you use to build a house. Around 26,000 bricks were packaged in boxes, assigned serial numbers, and placed on pallets. Auditors would see the product ready to ship and there were even plans to pretend to ship them to CompuAdd and CalAbco, two customers, who had agreed to accept and return the bricks on paper allowing them to absorb the $15 million write off a little at a time.
Unfortunately, the fictitious excellent financial performance led to an expectation of even better performance in the future which necessitated even further fraud. The company had turned around, but only on paper. A downturn in the computer business and maxed-out credit signaled the beginning of the end. Suppliers and employees weren’t getting paid. A senior manager violated insider trader rules and dumped a lot of stock.
The turnaround CEO finally resigned and a new CEO found the fraud and released the findings that they were in the hole for $100 million. Bankruptcy pushed the company’s assets to Maxtor and criminal charges against 16 people ensued ending in fines and jail time. It isn’t clear if any of the boxed bricks were shipped to anyone by accident or by a disgruntled employee with a rubber paycheck. [Tech Time Traveller] speculates that if someone has one, it would be quite the collector’s item.
We hear about companies doing questionable things, of course, but this really is impressive in scope. At least they weren’t scamming end users as some tech companies have done.
Continue reading “We’ve Heard Of Bricking A Hard Drive, But…”






 It all started when [Big Clive] ordered a chintzy Chinese musical meditation flower and found a black blob. But tantalizingly, the shiny plastic mess also included a 2 MB flash EEPROM. The questions then is: can one replace the contents with your own music? Spoiler: yes, you can! [Sprite_tm] and a team of Buddha Chip Hackers distributed across the globe got to work. (
It all started when [Big Clive] ordered a chintzy Chinese musical meditation flower and found a black blob. But tantalizingly, the shiny plastic mess also included a 2 MB flash EEPROM. The questions then is: can one replace the contents with your own music? Spoiler: yes, you can! [Sprite_tm] and a team of Buddha Chip Hackers distributed across the globe got to work. ( Bad pattern number one is XOR. Used correctly, XORing can be a force for good, but if you XOR your key with zeros, naturally, you get the key back as your ciphertext. And this data had a lot of zeros in it. That means that there were many long strings that started out the same, but they seemed to go on forever, as if they were pseudo-random. Bad crypto pattern number two is using a linear-feedback shift register for your pseudo-random numbers, because the parameter space is small enough that [Sprite_tm] could just brute-force it. At the end, he points out their third mistake — making the encryption so fun to hack on that it kept him motivated!
Bad pattern number one is XOR. Used correctly, XORing can be a force for good, but if you XOR your key with zeros, naturally, you get the key back as your ciphertext. And this data had a lot of zeros in it. That means that there were many long strings that started out the same, but they seemed to go on forever, as if they were pseudo-random. Bad crypto pattern number two is using a linear-feedback shift register for your pseudo-random numbers, because the parameter space is small enough that [Sprite_tm] could just brute-force it. At the end, he points out their third mistake — making the encryption so fun to hack on that it kept him motivated!