Radioactivity has always been a fascinating phenomenon for anyone interested in physics, and as a result we’ve featured many radioactivity-related projects on these pages over the years. More recently however, fears of nuclear disaster have prompted many hackers to look into environmental radiation monitoring. [Malte] was one of those looking to upgrade the radiation monitor on his weather station, but found the options for wireless geiger counters a bit limited.
So he decided to build himself his own Wifi and LoRa compatible environmental radiation monitor. Like most such projects it’s based on the ubiquitous Soviet-made SBM-20 GM tube, although the design also supports the Chinese J305βγ model. In either case, the tube’s operating voltage is generated by a discrete-transistor based oscillator which boosts the board’s 5 V supply to around 400 V with the help of an inductor and a voltage multiplier.
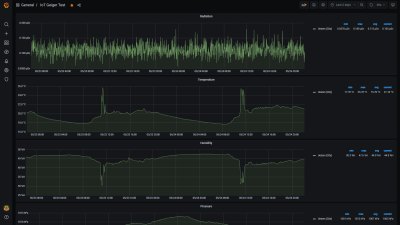
The tube’s output signal is converted into clean digital pulses to be counted by either an ESP32 or a Moteino R6, depending on the choice of wireless protocol. The ESP can make its data available through a web interface using its WiFi interface, while the Moteino can communicate through LoRa and sends out its data using MQTT. The resulting data is a counts-per-minute value which can be converted into an equivalent dose in Sievert using a simple conversion formula.
All design files are available on [Malte]’s website, including a PCB layout that neatly fits inside standard waterproof enclosures. Getting more radiation monitors out in the field can only be a good thing, as we found out when we tried to detect a radiation accident using community-sourced data back in 2019. Don’t like WiFi or LoRa? There’s plenty of other ways to connect your GM tubes to the internet.