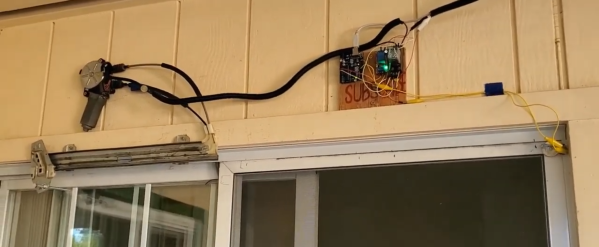
In many parts of the world leaving open a door or window is a good way to get a house full of bugs. Remembering to close doors behind them can be surprisingly hard for members of the human race, so the [DuctTape Mechanic] used the components from a car’s electric window to automate his sliding screen door.
After the excess pieces were cut off the rail, the motor and rail were mounted on top of the door frame. A long bolt is attached to the moving plate on the rail, which pushes on the pack of the door to close it. After closing, the mechanism returns to its open position, allowing the door to be opened by hand again. The motor is controlled by an Arduino running a very simple sketch, which senses if the door is closed with a microswitch and starts a 10 second countdown once opened. Two relays are used to create an H-bridge circuit to drive the motor in both directions.
It doesn’t look like there is any provision to detect if it is obstructed. A simple solution could be to make the push rod spring-loaded, so it can slide over the door if there is excessive resistance.
If you only want to let certain creatures into your house, we have no shortage of automated pet door for your hacking pleasure.
Continue reading “Electric Window Mechanism Into A Electric Screen Door”