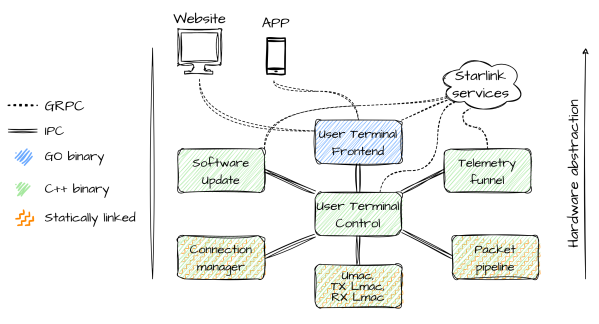
If there’s more to life than just a workshop full of tools, it’s probably a workshop full of tools that you’ve built yourself. At least that was the thinking behind the recently concluded “Gearing Up” challenge of the 2023 Hackaday Prize, which unsurprisingly generated quite a list of entries for our judges to review and whittle down to their top ten favorite tools, jigs, fixtures, and general labor-savers.
Having piqued the interest of our crack team of judges, these ten projects have not only earned a spot in the 2023 Hackaday Prize Finals, but they’ll also get a $500 cash prize to boot. But the heat is really on now; like all the finalists from the previous rounds, they’ve only got until October to get their projects as far along as they can before the final round. The grand prize is grand indeed — $50,000 in cash and a residency at the Supplyframe Design Lab in Pasadena!
We’re really getting down to the wire here, but it’s worth taking a little time out to look at some of the Gearing Up challenge winners, and what they came up with to make life in the shop a little easier. And don’t forget — the one who dies with the most tools wins!
Continue reading “Hackaday Prize 2023: The Gearing Up Challenge Finalists”