[Neil K. Sheridan]’s Automated Elephant Detection System was a semi-finalist in last year’s Hackaday Prize. Encouraged by his close finish, [Neil] is back at it with a refreshed and updated Elephant AI project.
The purpose of Elephant AI is to help humans and elephants coexist by eliminating contact between the two species. What this amounts to is an AI that can herd elephants. For this year’s project, [Neil] did away with the RF communications and village base stations in favor of 4G/3G-equipped, autonomous sentries equipped with Raspberry Pi computers with Go Pro cameras.
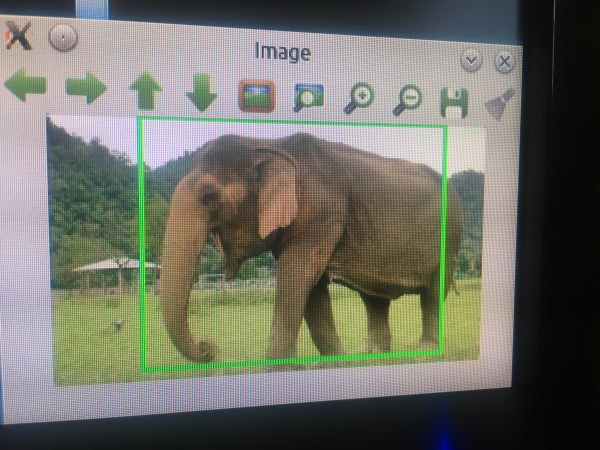
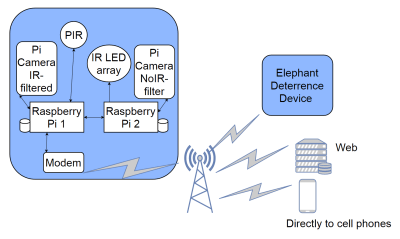 The main initiative of the project involves developing a system able to classify wild elephants visually, by automatically capturing images and then attempting to determine the elephant’s gender and age. Of particular importance is the challenge of detecting and controlling bull elephants during musth, a state of heightened aggressiveness that causes bulls to charge anyone who comes near. Musth can be detected visually, thanks to secretions called temporin that appear on the sides of the head. If cameras could identify bull elephants in musth and somehow guide them away from humans, everyone benefits.
The main initiative of the project involves developing a system able to classify wild elephants visually, by automatically capturing images and then attempting to determine the elephant’s gender and age. Of particular importance is the challenge of detecting and controlling bull elephants during musth, a state of heightened aggressiveness that causes bulls to charge anyone who comes near. Musth can be detected visually, thanks to secretions called temporin that appear on the sides of the head. If cameras could identify bull elephants in musth and somehow guide them away from humans, everyone benefits.
This brings up another challenge: [Neil] is researching ways to actually get elephants to move away if they’re approaching humans. He’s looking into nonlethal techniques like audio files of bees or lions, as well as ping-pong balls containing chili pepper.
Got some ideas? Follow the Elephant AI project on Hackaday.io.