E-cigarettes are increasingly popular, with weird hipster head shops popping up in towns around the globe. While you can buy this e-juice at gas stations and just about anywhere else analog cigarettes are sold, there are inevitably people who want to mix their own propylene glycol, glycerin, water, and nicotine. For them, [conklinnick] is building The End Of An Evil Industry, an e-juice printer that automates the entire process.
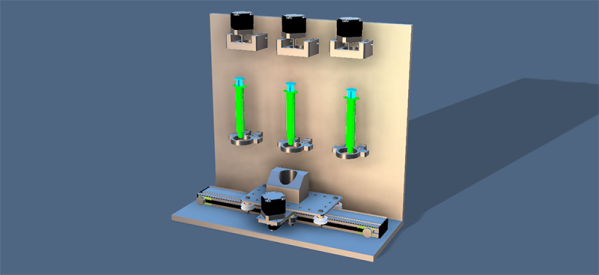
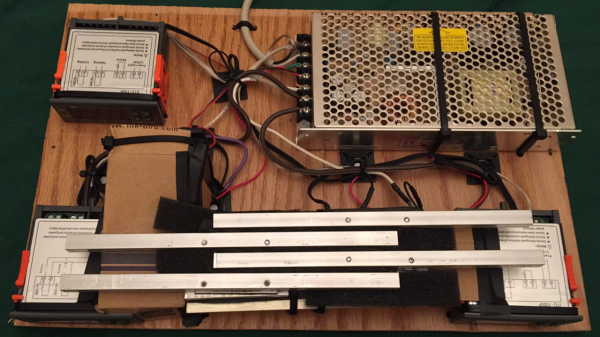
This ‘e-juice printer’ is designed to mix the basic ingredients of the consumables for e-cigarettes. These ingredients are propylene glycol and/or glycerin, water, flavorings, and nicotine. [conklinnick]’s project is using different ‘stations’ and a camera slider to dispense these ingredients into a small vial. It’s effectively a barbot dispensing ingredients for silly putty instead of alcohol.
It’s a great project, and although it’s not for everybody – nor should it be for everybody – it’s a great application of homebrew tech we already have for new uses.