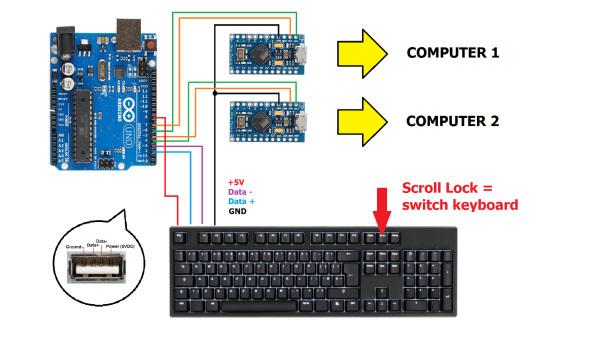
The Arduino platform is one of the most versatile microcontroller boards available, coming in a wide variety of shapes and sizes perfect for everything from blinking a few LEDs to robotics to entire home automation systems. One of its more subtle features is the ability to use its serial libraries to handle keyboard and mouse duties. While this can be used for basic HID implementations, [Nathalis] takes it a step further by using a series of Arduinos as a KVM switch; although admittedly without the video and mouse functionality yet.
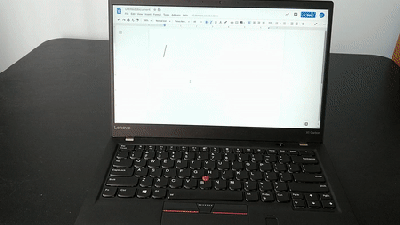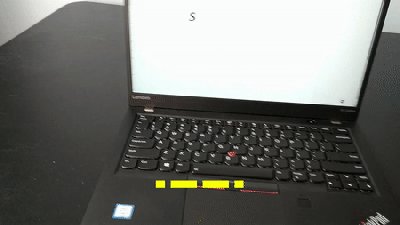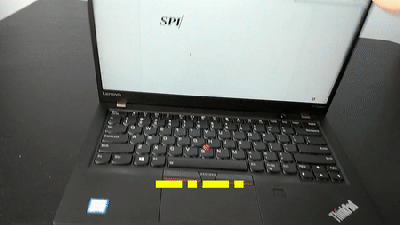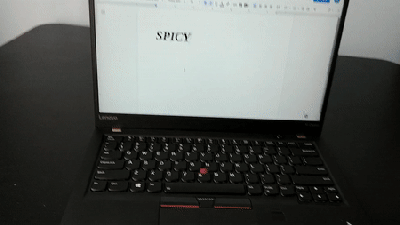
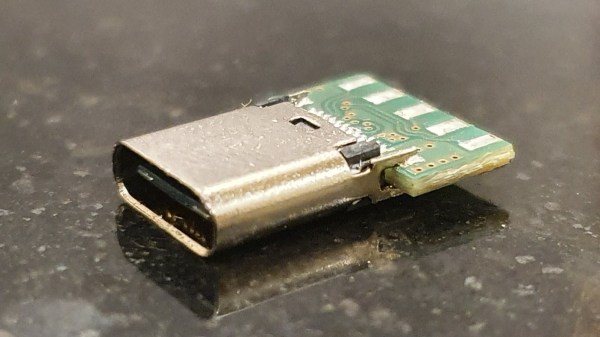
To start, an Arduino Uno accepts inputs from a keyboard which handles the incoming serial signals from the keyboard. From there, two Arduino Pro Micros are attached in parallel and receive signals from the Uno to send to their respective computers. The scroll lock key, which doesn’t do much of anything in modern times except upset Excel spreadsheeting, is the toggle switch between the two outputs. Everything is standard USB HID, so it should be compatible with pretty much everything out there. All of the source code and schematics are available in the project’s repository for anyone who wants to play along at home.
Using an Arduino to emulate a USB input device doesn’t have to be all work and no play, the same basic concept can also be used to build custom gaming controllers.


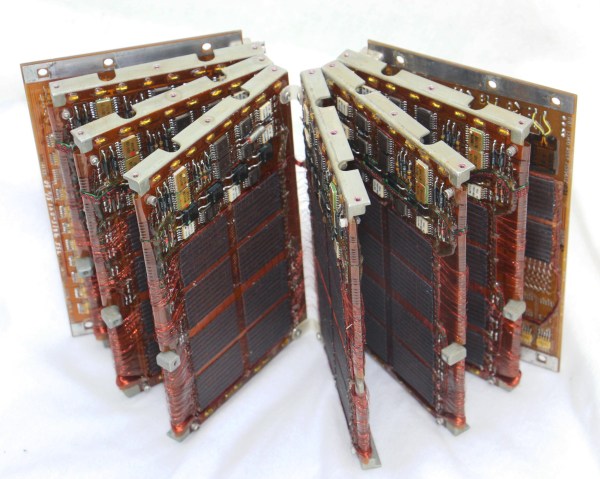
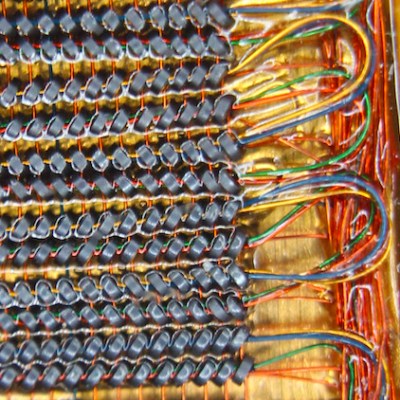 Amazingly these computers were composed of all digital logic, no centralized controller chip in this baby. That explains the need for the seven circuit boards which host a legion of logic chips, all slotting into a backplane.
Amazingly these computers were composed of all digital logic, no centralized controller chip in this baby. That explains the need for the seven circuit boards which host a legion of logic chips, all slotting into a backplane.