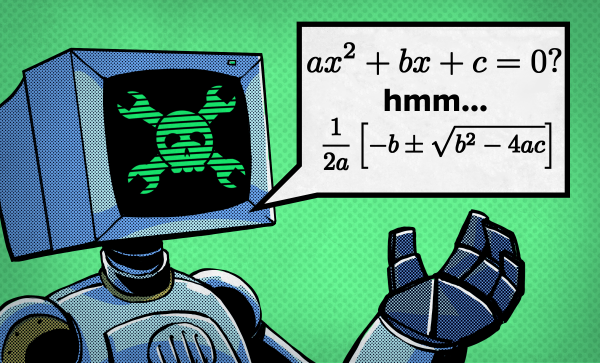
Don’t get me wrong. Like most people, there’s nothing I enjoy more than solving a long, involved math problem by hand. But, sometimes, a few pages of algebraic scratches on paper is just a means to an end. I find this especially true during electronic design sessions, be it circuit design or PCB layout; I just need the answer, and any time spent finding it distracts me from the larger task at hand. For me, at least, this seems to happen at least once a week, and about five years ago I decided to do something about it. I had heard of computer algebra packages, of course, but they weren’t taught as part of the undergraduate engineering curriculum when I went to school. So, I set about learning one: let the computers do the math!
The package I chose is wxMaxima, a document-based front-end to the Maxima computer-algebra system. Descended from code originally written in the late 1960s, it’s a general-purpose package supporting symbolic computation for algebra and calculus. There’s solid, mature code underneath with a modern UI veneer on top. Plus, it’s FOSS.
As I’ve progressed, I’ve found that some additional functions make the Maxima environment especially convenient for circuit design. A few are simple enough that I’d typically just re-create them as needed, so I never really got organized – there were several versions of my “library” floating around on various machines. I finally got my act together, cleaned up the most-frequently used functions, and put them into a GitHub repo.
Let’s have a look at how we can use them to take the tedium out of math for some design problems.
Continue reading “Computer Algebra For Electronic Design” →