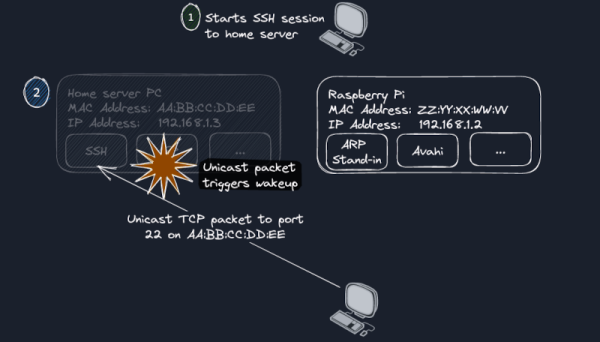
We all know we should save energy and not leave computers on all the time. It is probably better for the computer, too. But when you operate a home server, it isn’t feasible to just turn it on when you want to use it and then turn it off again. Or is it? [Daniel] decided that was exactly what he wanted to do, and it was quite an adventure to get there.
The trick is to use a Raspberry Pi — they don’t draw nearly the power a big computer does — to stay awake to facilitate the process. The Pi watches for ARP requests for the sleeping machine and replies on its behalf so that other network nodes can find the machine even when it isn’t on.
The server itself detects if it is idle in a cron job. When it finds that there are no SSH or other service connections for a set period of time, it suspends the machine to RAM, putting it in a low-power mode. Waking a sleeping computer up over the network is a solved problem, and [Daniel] investigated several wake-on-lan solutions.
There were several oddities to work out, including a Mac pinging an unused network share, and a router that was making NetBIOS queries. However, [Daniel] found a $30 router that could do port mirroring and that helped a lot with troubleshooting.
This is one of those things where his recipe won’t exactly fit your situation. But the post has a lot of good information and some nice tricks for troubleshooting any kind of network bizarreness.
Wireshark is a great tool for this kind of work, too. Another useful technique is recording network traffic and playing it back.